In this thread I will reverse engineer a crackme on Android of
We will solve the crackme number 2, to install it in our emulator we use the android device bridge
We upload it with adb push 'local' 'emulator'
We open shell in the emulator with adb shell
Navigate to the directory where we have uploaded the APK
We install with adb install package_name
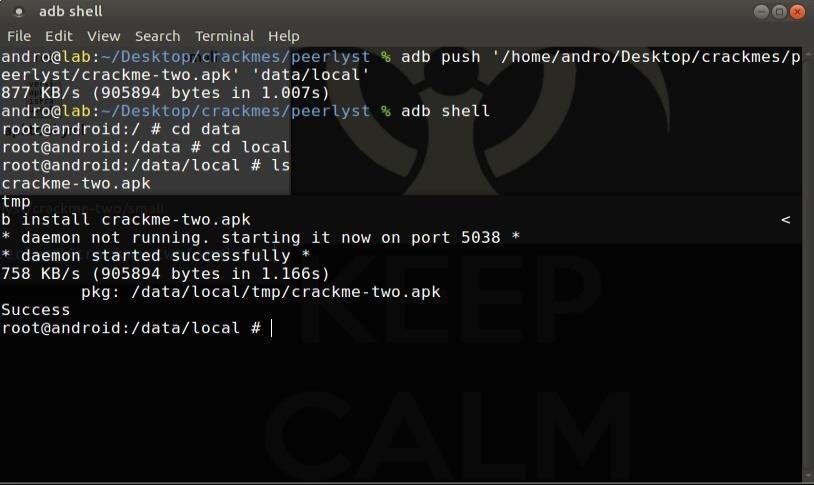
The crackme presents the following panel of login where it asks for an email and a password (secret):
The next thing we will do is locate the system console in the directory where we installed the apk and write apktool d package_name
Once the apk has been decompiled, we enter the folder that has been created and later in the smal directory
Once we are in the smali directory we grep -R -i password
With this command we will search in all directories recursively the string password without case sensitive (-i)
What we are looking for are hardcode strings containing password to see if we can pull the thread from there.
We should draw attention to the following line
const-string v8, "Leaving debug code in your application can be dangerous, let alone unsalted password hashes."
To see more concretely to which comes this line we must navigate to the route indicated in purple.
Once inside we can see the file in smali code
Note:
- the smal code is the midpoint between the code programmed in Java and the dalvik code that is the one that "understands" the android virtual machine when running the application.
In line 191 we find the string that we were looking for, and a little further down should call attention to the following line also hardcode
const-string v8, "WARN Secret didn \ 't match b2c4782f0afc0d9ccf21af70ac6c5c7e"
This is a log error message generated after comparing two MD5 hashes, this hash that compares is the password (secret) we have entered, so for pure logic, if we decrypt the hash we will have the password.
Now we lack the access email, but if in that same file we look @ we jump directly to another hardcode line with an email.
We already have the email and password (secret), try to login ...
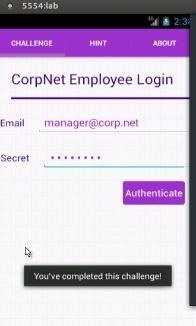
Done :)
Until next time








































Be the First to Respond
Share Your Thoughts