Hello and welcome to my very first tutorial series ! Its goal is to learn you how to make your own fully functional hacking tool, including shell access to the target, uploading/downloading files, keystrokes record and many other features that will be detailed later in this introduction article.
Why Rewriting Tools That Already Exists ?
Every utility we are going to code is already implemented in many other tools such as Meterpreter in Metasploit. So, why should we bother creating our own stuff which will probably be less efficient that the one created by a team of security experts ? I believe it is essential to know how the tools you are using actually work in order to customize them along your needs. In addition, it is a good opportunity to learn new stuff about programming in general, which I personnaly always find super cool !
Why Python ?
Using a langage or another is in general quite arguable. What made me chose Python is its abilty to make complex actions easily (at the risk of loosing a part of comprehension..) thanks to its huge choice of well documented libraries (more than 100.000 !), either implemented by default or made by its large community. Python is also well-known for its easy syntax which can save you a lot of time, both for writing and reading code. This xkcd sums up pretty well my opinion about it :
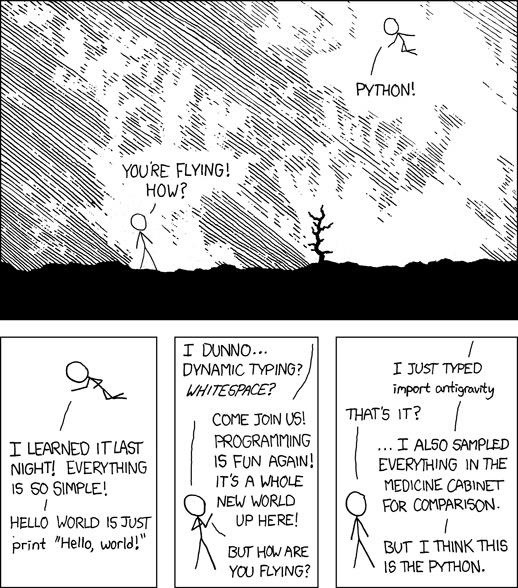
Finally Python philosophy matched my ideas of how programming should be done. Anyway I am sure other "scripting" languages like Ruby would be able to do exactly the same. If you are not familiar with Python syntax you can read this "Learn Python in 10 minutes" tutorial that will makes you a bit more comfortable with what you will read in this tutorial series.
Key point : I will be using Python 2.7 because some of the modules I use have not been officially ported to Python 3 yet. If you still prefer to use Python 3 you shouldn't encounter big issues with what we are going to do, except a few syntax changes.
Tutorial Series Organization
This tutorial will be devided in a still unknown number of articles which should cover the following topics :
- Interacting with the target via a remote shell (Part 1)
- Priviledge escalation
- Upload/Download files and directories from target
- Information gathering (especially stored passwords)
- Keylogger
- Webcam snapping (and streaming ?)
- Handling multiple targets at the same time
- Combining all those features in one single interactive program
- Delivering the backdoor
Each part of the tutorial will present a Python implementation of one of those features, links to the corresponding articles will be added as I go along so this page can be used as a summary. (By the way is it normal that I can't publish a "How-To" but only a Forum Thread ?)
Post Scriptum
Because this is the very first tutorial I have ever written on the internet I assume it might not be as good as you could except but hey, you have to start somewhere and null-byte community seemed to be respectful enough for beginners like me. In fact I am quite new to cyber security and computing in general. I have 2-3 years of coding and have been interesting in security for only 6 month so there might be some innacurate informations here and there but I will do my best to avoid it. I believe sharing the few knowledge is the best way to improve myself thanks to your advises, so don't hesitate to point out anything that could be done better or suggest ideas to improve the code. Finally I wanted to mention that english is not my native language so there might be a few mistakes but I am doing my best to make it as readable as possible.
See you soon for the first tutorial that will teach you how to get a shell acces on the target that I will publish within a day or two.








































Be the First to Respond
Share Your Thoughts