I tried doing a metasploit exploitation using a payload created with veil-evasion. This payload worked with other computers in my own network and with the computer of a friend of mine. Nevertheless it didn't work when I tested it with computer science with permission of the teacher.
- I made the payload with Veil-Evasion.
- payload: python/shellcodeinject/base64substitution
- extension is .exe
- IP= public IP
- Port = forwarded
- School might be using their own server?
- I tried pinging the IP of the target and it responds well.
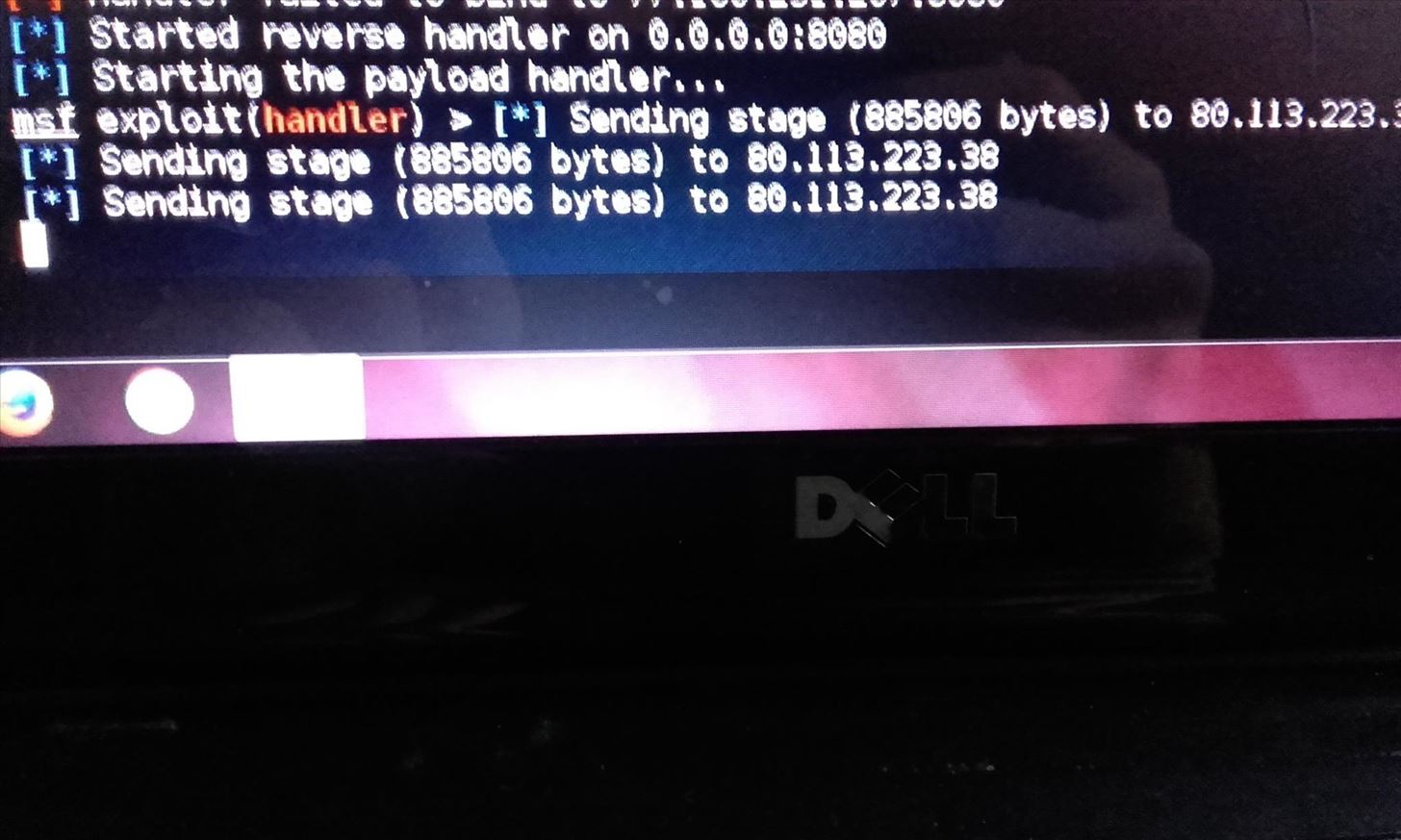
This is what I get:
but no meterpreter sessions is started.
Does anyone know how to solve this?








































8 Responses
The school may have a firewall that is blocking the stage from being received by the victim.
-Defalt
I thought maybe getting in the same network as the victim with my computer might solve the problem but I don't know if you are talking about a firewall on the computer or a network firewall.
Do you have any ideas about getting around this?
A network firewall most likely. I see you've bound your handler to port 8080, you may try using a well known port such as 80 or 443.
-Defalt
Thanks, but was I right about bypassing this firewall when entering the same network with my host machine?
It all depends on the network topolgy. If the firewall filters traffic between subnets, then you'll need to be on the same subnet. But if the firewall filters traffic coming from the Internet only, you won't need to be.
In short, maybe.
-Defalt
Thanks a lot
Not knowing the environment I would have to guess that something is blocking the second stage of the payload.
Edit: Submitted without seeing above comment.
This happened on my school network, too.
Failed to bind IP...
Share Your Thoughts