Hello guys, here for my first post ever on null byte, hoping i dont go full retard with my questions and that these haven't been answered before. (i don't think they have)
I recently moved and while i was at it i changed ISP and got a brand new router from them. The router from my previous ISP was heavily pressured by myself trying all the great tuts on hacking wifi OTW has made here. But as i tried some of this stuff on the new one, i stumbled on an issue i hadnt encountered on the two routers i had previously experienced on.
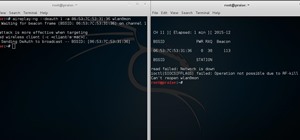
Now i saw messages like this appear when trying to reaver or bully that damn router after 3 pin attempts.
! WARNING: Detected AP rate limiting, waiting 60 seconds before re-checking
I guess its pretty normal ap manufacturers started implementing some security.
So i searched my way on the internet trying to find out how to bypass this.
First attempted to check if router was mac locking by making a script that would stop reaver and change the mac everytime it locked, wasnt the case, changing mac didnt undo the lock.
Then i found some post on kali forums that explained you could use MDK3 to reboot the router and maybe bypass the lock for a few minutes, going the manual way through the mdk3 commands i couldn't get my router to reboot.
Then tried Revdk3 script that was able to reboot my router but still ddint allow me more than 3 pin attemps at each reboot of the router (which makes for a pretty long crack you'd agreee).
This is why i was wondering if any of you fellow apprentice hackers or the master hackers knew about this issue, had experienced it, and if you could share data about what you have found to resolve it.








































7 Responses
Merci de la réponse, en effet je suis francais! (peut etre que mon nom est un peu trop flag) mais bon du coup je m'en fous pour mon routeur mais les ISP francais sont vraiment bons en sécurité wifi alors?
Like he is saying try and change the MAC but that really won't help. Add delay option and hope for the worst. Expect it to take 9 mos to crack. Honestly If this is a newer AP 5% chance. Really all advice out now days is snake oil on new APs.
Oh ok!
Side note . I got 3 last week in tests to gimme pins to 100%. Password lists can work if you get a Valid handshake. It may say handshake captured but it most likely have not yet. You will need to cross check the Cap file.
Now I agree with that.
It's not a surprise considering so many routers were being shipped with ridiculously vulnerable firmware and no patches being implemented.
ghost_
Different routers will have different WPS protections regarding pin attacks. Some will have a general "3 attempts and all are locked out" feature, some will lock out only the mac address of the attacking machine, etc. If the router is one that locks only the attacking mac address, a simple script that will use reaver to attack twice and then shutdown the interface and either change the mac or create a new virtual interface with spoofed mac and then resume the attack repeating the process until the pin has been found. However, if the WPS lockout is for all pin attempts, the mac cloning and virtual interface creation methods won't work. You will instead need to incorporate a script that will fully reboot the router. Even under a full reboot, the lock out may still be in effect.
I am researching a method to force a reset instead of a reboot and from this we simply are able to use default router admin name and password and can fully login to the router using any browser.
I guess by DOS attacks you can actually make anybody go and reset the router as he or she won't be able to connect to the internet and the only option would be to reset the router
Share Your Thoughts