Here is an alternative to using Tor Browser and Proxychains
What does it do:
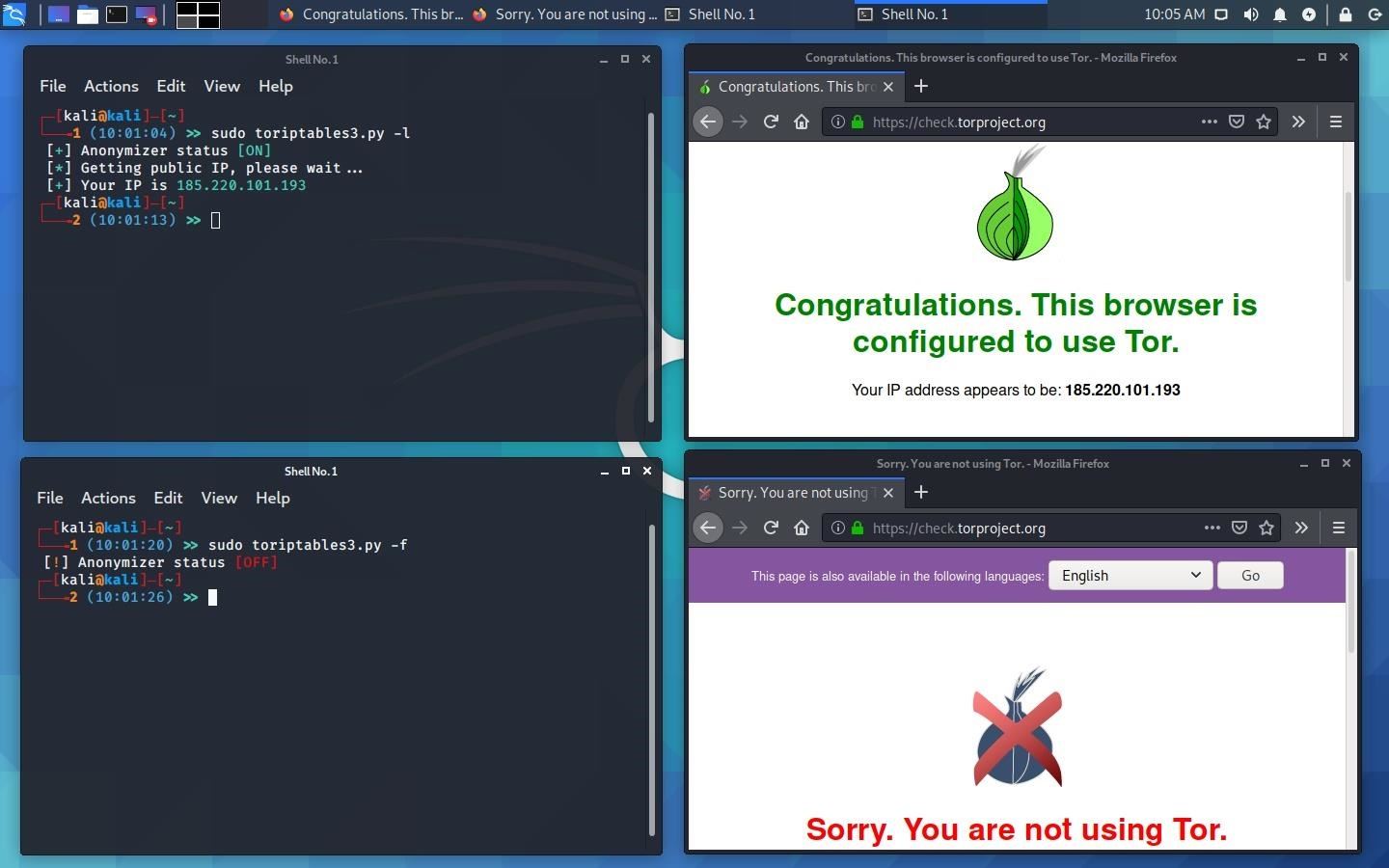
Tor transparent routing, routes traffic through Tor using Iptables ruleset.
This will route all traffic on a standalone machine through the Tor network.
All application will make its TCP connections through Tor on port tcp/9040.
All DNS requests are resolve through Tor to avoid anonymity compromised by DNS leaks.
Pros:
Can work in conjunction with Tor Browser and Proxychains
No third party (NSA backdoored) software
No visual proof of having an anonymizer on your system
Zero configuration
Cons:
Have to set a cron job to reload tor service at your preferred interval
Dependencies:
tor
Usage:
toriptables2.py -h
toriptables3.py -h
To test:
ifconfig.me
whatismyipaddress.com
check.torproject.org
dnsleaktest.com
The scripts can be found here:
github.com/ruped24/toriptables2
github.com/ruped24/toriptables3
By: n0neXn0ne








































8 Responses
How anonymous is this? Is it like Tails?
As for anonymity, it works pretty well. The problem is that ToR has been compromised by NSA and other governments.
Yeah but it's not a problem for me. My third world government don't know about anything. Besides, I first start my no log offshore vpn(encrypt all data) then connect to tor network. Does it not protect me from exit node detection by ISP?
NSA watches everyone's traffic.
No
The point I'm trying to make is instead of using only the vpn, using tor over the vpn isn't more secure? I mean that has to add some security level compared to using only our vpn. Besides, they can't trace back to me without compromising my mixed bitcoin paid offshore vpn. I'm not saying it's impossible but using different methods together can make the things(public network from far with yagi +no log vpn + proxychains +tor) harder for them.
And I don't do that much nasty things to get NSA to the work.
Sounds like you should be pretty secure
Kudos! Great article! :D
Share Your Thoughts