Actually there's a little way you can do when someone's using Wireshark in a network, because wireshark only collects packet data in a passive mode or let's say it's just collecting and grabbing the data that comes across the network.
This Wireshark will works perfectly on network that using WI-FI and HUB because the packet sent and received are also sent to another computer inside the network. If you still can't get what I mean, please see the illustrations below.
When you're using HUB, the data sent inside and outside the network will come through HUB, but the main problem is: HUB will forward all packet into the entire network and checks if a device owns the packet or not. If there's a device owns the packet, then it will ACCEPT it and the others will DROP the packet.
By using this method, all computers in the network will absolutely receive the packet but will drop it because the packet was not addressed to them. In this network Wireshark will act as data collector and grab all the data even the data which was not addressed to them.
In this type of network, Wireshark will also act as data collector across the network(especially on network that does no't have data encryption
Detecting Sniffing Devices Using Nmap #1
The Attacker -> Kali Machine ... Any machine with WireShark
Us { Victim } -> Kali Machine ... Any machine with WireShark
The Attacker's Desktop ... Starting WireShark
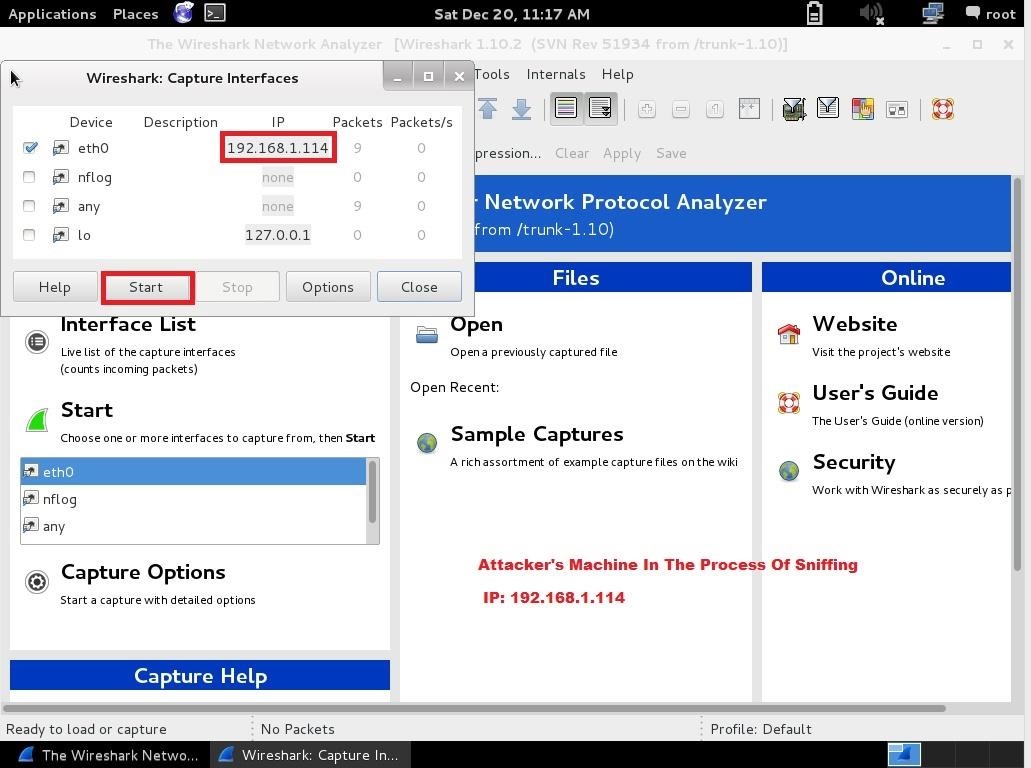
Attacker Sniffing In Progress
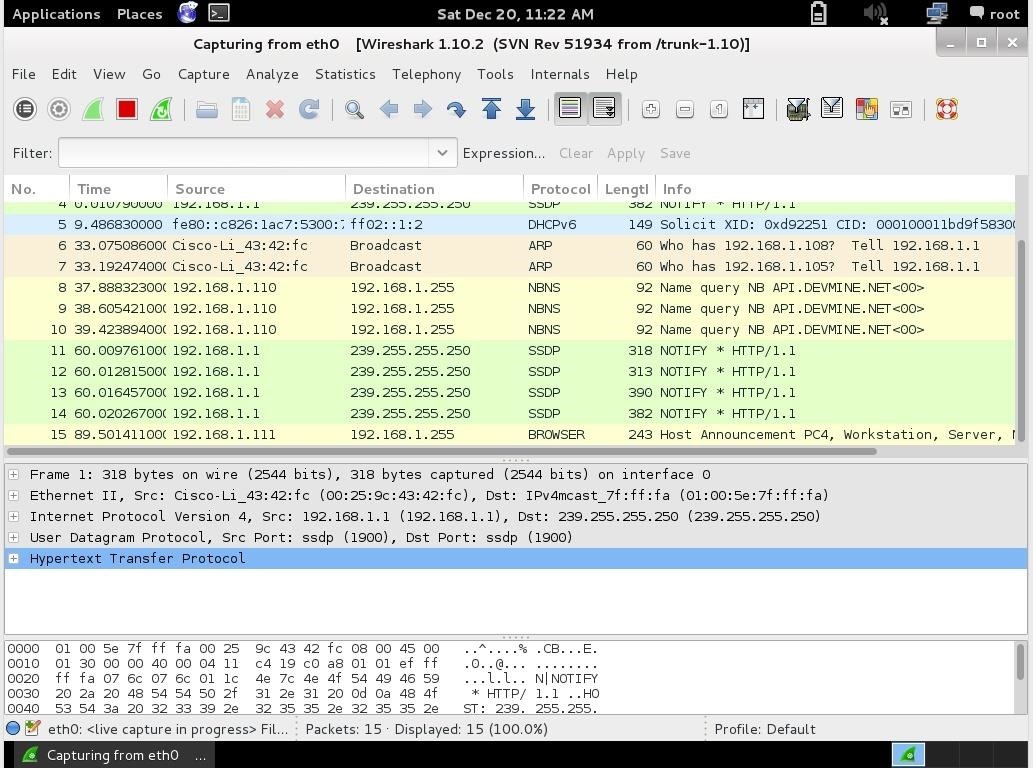
Now Let's Take Note of Some few details from the attacker:
IP: 192.168.1.114
Mac Address: 08:00:27:e9:2b:78
IPv6: fe80::a00:27ff:fee9:2b78
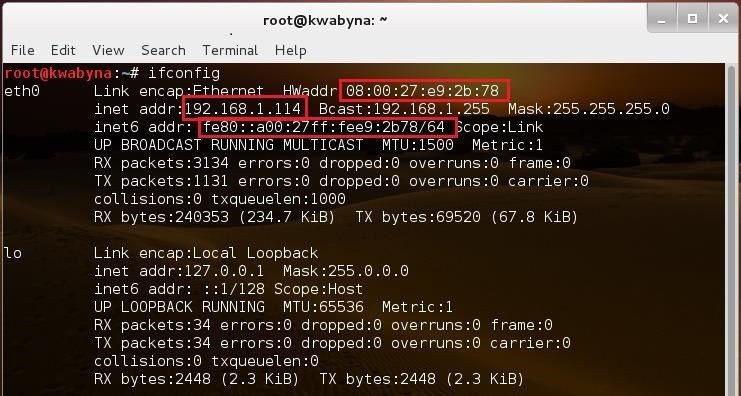
Victim { Us } Using NMAP To Detect Attacker
Drop your terminals and hit the nmap detect-sniffer command
#> nmap --script=sniffer-detect 192.168.1.0/24
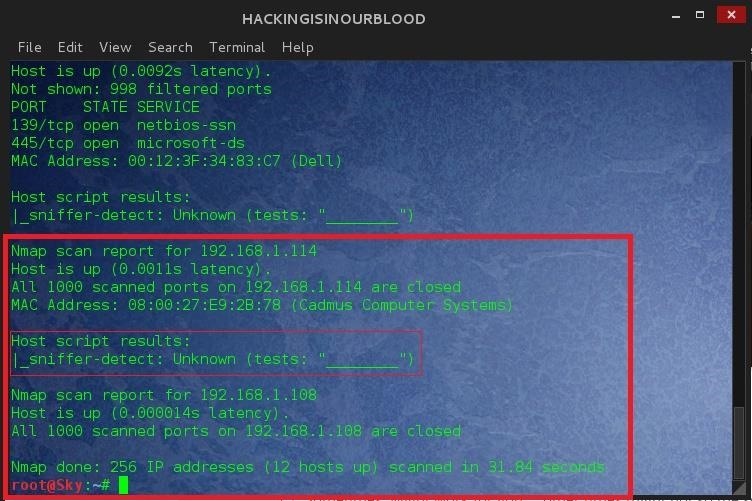
Sometimes: Might work for you ... other times might not so the solution is to try every ip manually.. Replace the entire network thing with the ip.
#> nmap --script=sniffer-detect 192.168.114
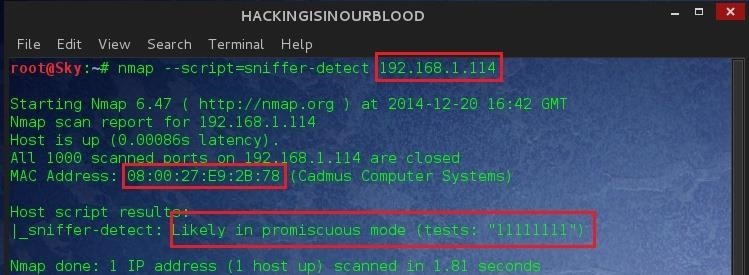
We can see that the system has been detected to be running in promiscuous mode and the result is "11111111." Different operating systems report different combinations of 1's. Linux reports "11111111", Windows 2k, XP, Vista, and Windows 7 reports "111_1_". By default, the script will only report NICs Likely in promiscuous mode so if you don't see get any results, that's because the scan returned false.
Our Scan Result Shows:
IP: 192.168.1.114
Mac Address: 08:00:27:e9:2b:78
Which matches the details we gathered above ... Hope you didn't have a hard time.
Detecting Sniffing Devices Using Detect_Sniffer #2
Opening Detect_Sniffer In Kali
Detect Sniffer Interface
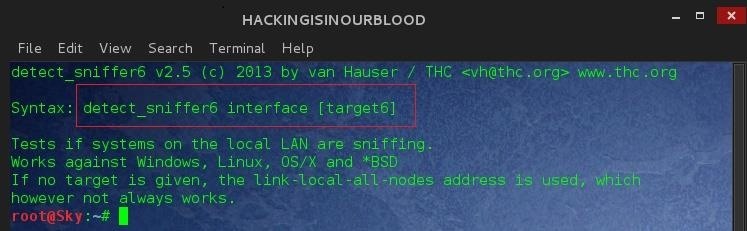
Should You Know The Attacker's IPv6 Address
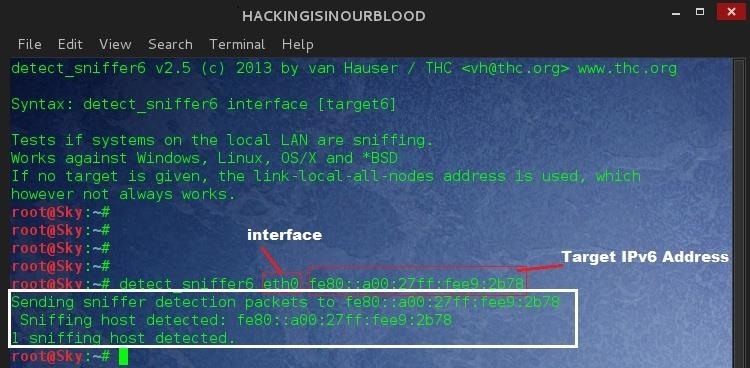
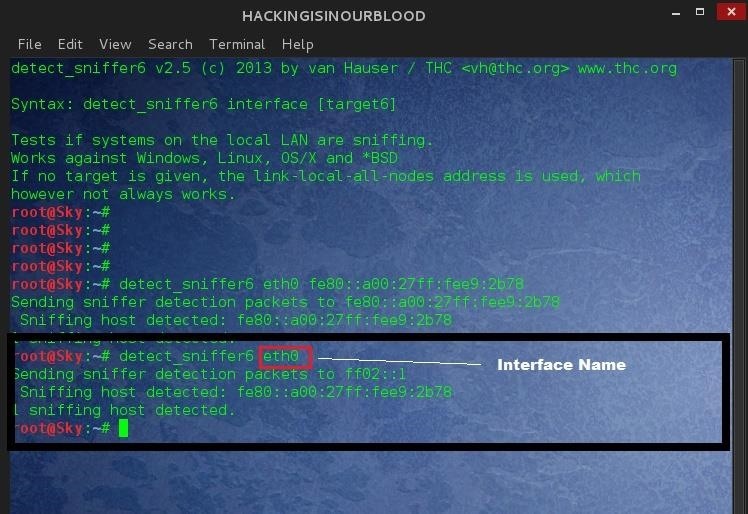
#> detect_sniffer6 eth0 fe80::a00:27ff:fee9:2b78
- eth0: Network Interface
- fe80::a00:27ff:fee9:2b78: Target IPv6 Address
Should You Not Know The Attacker's IPv6 Address
Easy: Try inserting the network interface without address
#> detect_sniffer6 eth0
- eth0: Network Interface
Conclusion
And maybe it was better if you do preventive actions for your network. Below are some ways to prevent such attacks as I think (You can add other suggestion for me to put in this article).
- Host to host encryption (IPSEC)
- Use encrypted protocols (SSL,FTPS,SSH)
- Use switch for your network
This is how we can use this tool , hope you learn something new and now before joining any new network , you use this tool to detect network sniffer.
Be creative , think creative and keep learning.
Hope it's useful.
Correct me for any error i made any error.
Stay Calm And Hack The Planet
peace-out
#Sky









































1 Response
Alright
Share Your Thoughts