The following 'How To' will detail how to configure an attack over WAN while using a VPN to hide your real IP address and a DDNS provider to make your IP static. It will also cover how to appropriately set your LHOST and LPORT.
For this tutorial, you need:
- VPN with port forwarding. Try privateinternetaccess.com
- A DDNS like noip.com
- Port checking tool. Try portchecktool.com
- Netcat
For exploitation and post exploitation activities across WAN, a covert channel must be established between the attacking computer (Kali) and compromised target. For this Kali needs a static IP address and an open port. From an OpSec perspective, connecting back to your own computer is not a good look. You probably want to use a VPN to mask your real IP address. I use and recommend Private Internet Access. It's very inexpensive and includes the ability to port forward.
Step 1: Connect to VPN, Choose Port Forwarding
Launch Private Internet Access and select a port-forward enabled gateway to connect to, CA Montreal or CA Vancouver for example. Not all of PIA's gateways are port forward enabled.
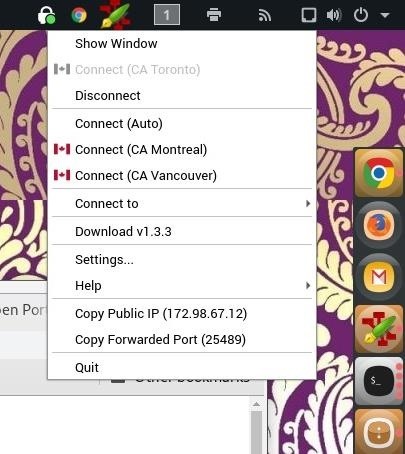
*Always connect to your VPN FIRST before syncing your IP with your DDNS.
Step 2: Create a DDNS Hostname
Sign up for an account with a Dynamic DNS provider like No-IP. From your Dashboard, create a Hostname and domain. I've elected panthertin.ddns.net.
*Using the picture below as a reference, make sure the 'IP/Target' of your newly created hostname matches that given to you by your VPN.
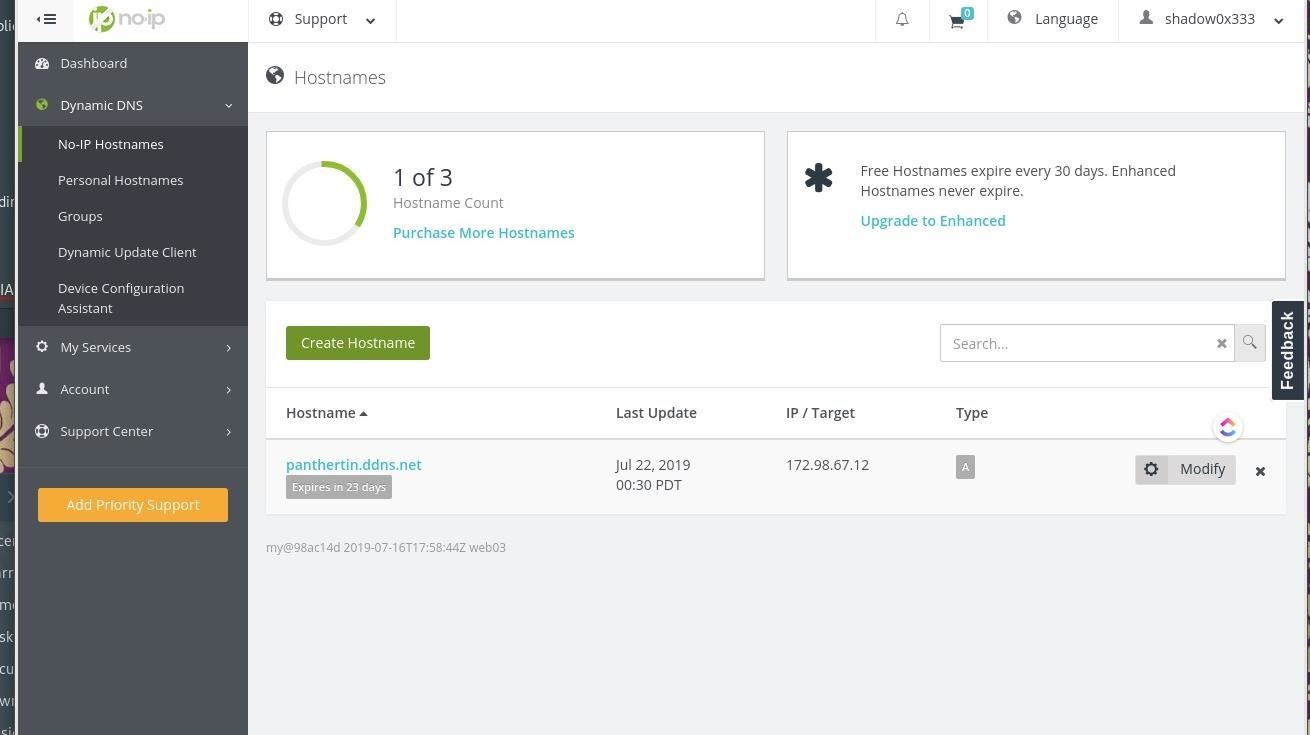
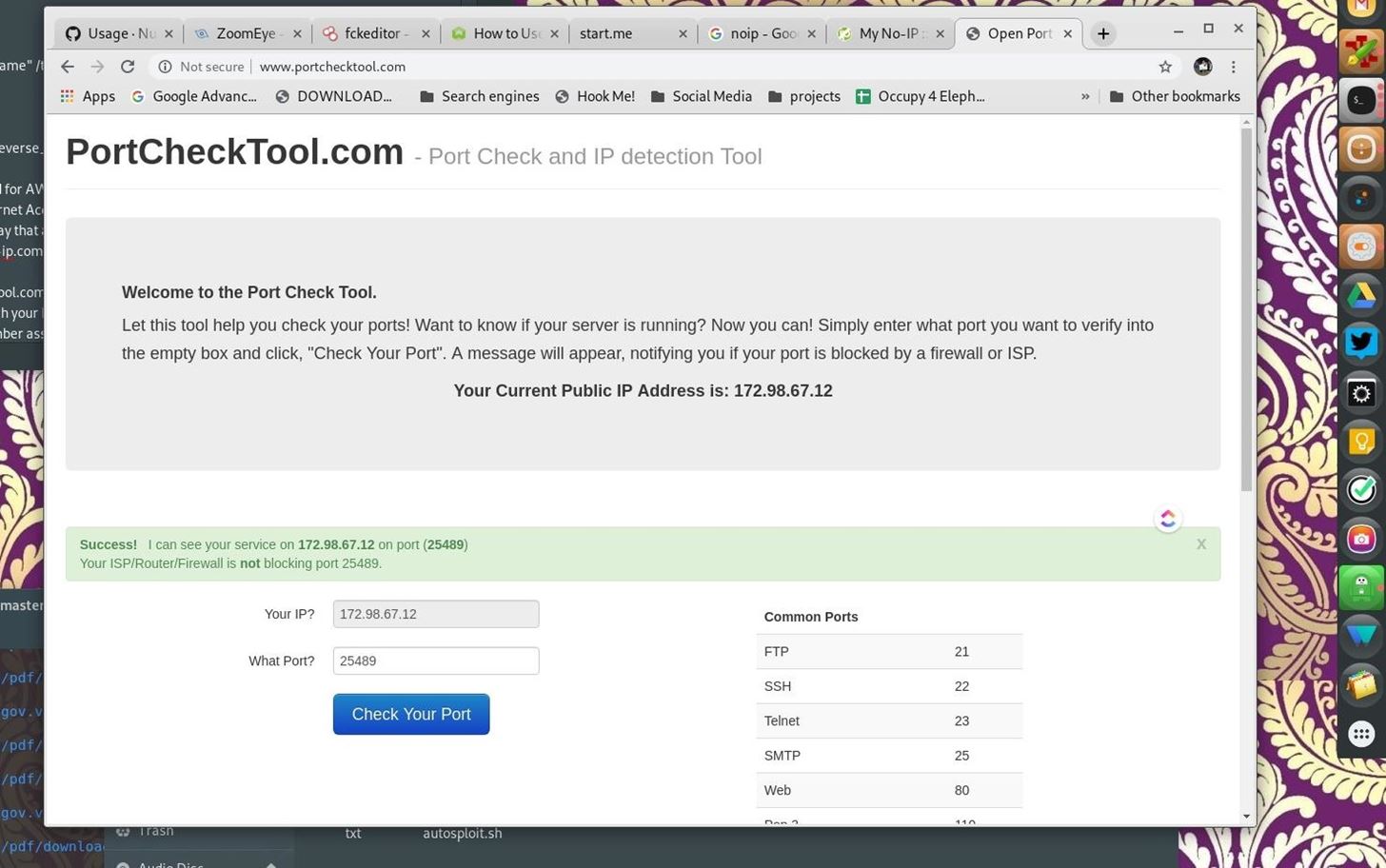
Step 3: Verify Port Forwarding
Verify port forwarding is working correctly by:
- In terminal, use netcat to launch a listener on the forwarded port assigned by VPN, in my case it is 25489
nc -l 25489
- Visit portchecktool.com
- The pre-populated IP address should match the one assigned to you by your VPN
- Enter the forwarded port number assigned by your VPN
- Click 'Check your Port' button. It should say:
Step 4: Set LHOST and LPORT
When configuring payloads for Metasploit or some other exploit framework, your LHOST will be your DDNS hostname/IP address and your LPORT will be the forwarded port given to you by the VPN.
That's it! Easy!
Remember, it is ILLEGAL to hack! You must get explicit consent from owner in all circumstances!









































2 Responses
So, to set the listener, it's the same thing? put the port forwarded of the vpn and the static ip? in case of a reverse tcp
Why not use something like ngrok?
Share Your Thoughts