I know what encorders are and why they are there but how do they work? What I know is that they change the signature of what it is used on. How do they do so? Do they add random code and comments to change their hash? Or does it change how compiled exploits are compiled?
Forum Thread: Metasploit Encoders
- Hot
- Active
-
 Forum Thread:
When My Kali Linux Finishes Installing (It Is Ready to Boot), and When I Try to Boot It All I Get Is a Black Screen.
8
Replies
Forum Thread:
When My Kali Linux Finishes Installing (It Is Ready to Boot), and When I Try to Boot It All I Get Is a Black Screen.
8
Replies
1 day ago -
 Forum Thread:
HACK ANDROID with KALI USING PORT FORWARDING(portmap.io)
12
Replies
Forum Thread:
HACK ANDROID with KALI USING PORT FORWARDING(portmap.io)
12
Replies
1 wk ago -
 Forum Thread:
Hydra Syntax Issue Stops After 16 Attempts
2
Replies
Forum Thread:
Hydra Syntax Issue Stops After 16 Attempts
2
Replies
4 wks ago -
 Forum Thread:
Hack Instagram Account Using BruteForce
208
Replies
Forum Thread:
Hack Instagram Account Using BruteForce
208
Replies
1 mo ago -
 Forum Thread:
Metasploit reverse_tcp Handler Problem
47
Replies
Forum Thread:
Metasploit reverse_tcp Handler Problem
47
Replies
2 mo ago -
 Forum Thread:
How to Train to Be an IT Security Professional (Ethical Hacker)
22
Replies
Forum Thread:
How to Train to Be an IT Security Professional (Ethical Hacker)
22
Replies
2 mo ago -
 Metasploit Error:
Handler Failed to Bind
41
Replies
Metasploit Error:
Handler Failed to Bind
41
Replies
3 mo ago -
 Forum Thread:
How to Hack Android Phone Using Same Wifi
21
Replies
Forum Thread:
How to Hack Android Phone Using Same Wifi
21
Replies
3 mo ago -
 How to:
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
177
Replies
How to:
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
177
Replies
3 mo ago -
 How to:
Crack Instagram Passwords Using Instainsane
36
Replies
How to:
Crack Instagram Passwords Using Instainsane
36
Replies
3 mo ago -
 Forum Thread:
How to Hack an Android Device Remotely, to Gain Acces to Gmail, Facebook, Twitter and More
5
Replies
Forum Thread:
How to Hack an Android Device Remotely, to Gain Acces to Gmail, Facebook, Twitter and More
5
Replies
3 mo ago -
 Forum Thread:
How Many Hackers Have Played Watch_Dogs Game Before?
13
Replies
Forum Thread:
How Many Hackers Have Played Watch_Dogs Game Before?
13
Replies
3 mo ago -
 Forum Thread:
How to Hack an Android Device with Only a Ip Adress
55
Replies
Forum Thread:
How to Hack an Android Device with Only a Ip Adress
55
Replies
4 mo ago -
 How to:
Sign the APK File with Embedded Payload (The Ultimate Guide)
10
Replies
How to:
Sign the APK File with Embedded Payload (The Ultimate Guide)
10
Replies
4 mo ago -
 Forum Thread:
How to Run and Install Kali Linux on a Chromebook
18
Replies
Forum Thread:
How to Run and Install Kali Linux on a Chromebook
18
Replies
5 mo ago -
 Forum Thread:
How to Find Admin Panel Page of a Website?
13
Replies
Forum Thread:
How to Find Admin Panel Page of a Website?
13
Replies
6 mo ago -
 Forum Thread:
can i run kali lenux in windows 10 without reboting my computer
4
Replies
Forum Thread:
can i run kali lenux in windows 10 without reboting my computer
4
Replies
6 mo ago -
 Forum Thread:
How to Hack School Website
11
Replies
Forum Thread:
How to Hack School Website
11
Replies
6 mo ago -
 Forum Thread:
Make a Phishing Page for Harvesting Credentials Yourself
8
Replies
Forum Thread:
Make a Phishing Page for Harvesting Credentials Yourself
8
Replies
6 mo ago -
 Forum Thread:
Creating an Completely Undetectable Executable in Under 15 Minutes!
38
Replies
Forum Thread:
Creating an Completely Undetectable Executable in Under 15 Minutes!
38
Replies
7 mo ago
-
 How To:
Find Identifying Information from a Phone Number Using OSINT Tools
How To:
Find Identifying Information from a Phone Number Using OSINT Tools
-
 How To:
Exploit EternalBlue on Windows Server with Metasploit
How To:
Exploit EternalBlue on Windows Server with Metasploit
-
 BT Recon:
How to Snoop on Bluetooth Devices Using Kali Linux
BT Recon:
How to Snoop on Bluetooth Devices Using Kali Linux
-
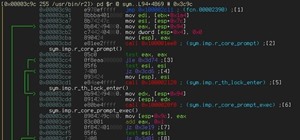 How To:
Reverse Engineering with Radare2 (A Quick Introduction)
How To:
Reverse Engineering with Radare2 (A Quick Introduction)
-
 How To:
Perform an Attack Over WAN (Internet)
How To:
Perform an Attack Over WAN (Internet)
-
 How To:
Use Burp & FoxyProxy to Easily Switch Between Proxy Settings
How To:
Use Burp & FoxyProxy to Easily Switch Between Proxy Settings
-
 How To:
Crack SSH Private Key Passwords with John the Ripper
How To:
Crack SSH Private Key Passwords with John the Ripper
-
 How To:
Make Your Own Bad USB
How To:
Make Your Own Bad USB
-
 How To:
Find Passwords in Exposed Log Files with Google Dorks
How To:
Find Passwords in Exposed Log Files with Google Dorks
-
 How To:
Gain SSH Access to Servers by Brute-Forcing Credentials
How To:
Gain SSH Access to Servers by Brute-Forcing Credentials
-
 Hack Like a Pro:
How to Find Directories in Websites Using DirBuster
Hack Like a Pro:
How to Find Directories in Websites Using DirBuster
-
 How To:
Exploring Kali Linux Alternatives: Getting Started with Pentoo for Advanced Software Installations
How To:
Exploring Kali Linux Alternatives: Getting Started with Pentoo for Advanced Software Installations
-
 How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
-
 How To:
Exploit Java Remote Method Invocation to Get Root
How To:
Exploit Java Remote Method Invocation to Get Root
-
 How To:
Control Anything with a Wi-Fi Relay Switch Using aRest
How To:
Control Anything with a Wi-Fi Relay Switch Using aRest
-
 Hack Like a Pro:
How to Scan for Vulnerabilities with Nessus
Hack Like a Pro:
How to Scan for Vulnerabilities with Nessus
-
 How To:
Dox Anyone
How To:
Dox Anyone
-
 How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
-
 How To:
Find Vulnerable Webcams Across the Globe Using Shodan
How To:
Find Vulnerable Webcams Across the Globe Using Shodan
-
 How To:
Check if Your Wireless Network Adapter Supports Monitor Mode & Packet Injection
How To:
Check if Your Wireless Network Adapter Supports Monitor Mode & Packet Injection














7 Responses
Think of it like this...
Youre like a thief.. av is the police.. av is shooting at you... now encoders are your kevlar.. your shield.... the better your shield.. the better chance of your survival..
The encooder masks your exploit under itself.. probably code..
And no it doesnt change how exploits are compiled..
So it covers the exploit as another program/protocol or whatever? How though?
Jeremiah:
AV software is looking for a signature of the malware. If we re-write the code with the same functionality or encrypt the code, sometimes it can get past the AV,
Ok thank you for the explanation. If the payload is encrypted what decrypts it? Does the exploit decrypt it or does it send a smaller payload to decrypt it?
In the simplest cases, the payload is XORed.
Ah ok, so this is one way an advanced AV could still detect the payload?
Of course. Nowadays AVs use templates and encoder templates, so you will have to do some more magic in order to get past it.
Share Your Thoughts